In today’s digital landscape, cybersecurity is paramount for businesses of all sizes. Firewalls serve as the first line of defense against cyber threats, ensuring that sensitive data remains protected from unauthorized access. Elysian Communication Private Limited offers expert firewall configuration services to enhance network security, optimize performance, and safeguard critical business operations.
Why Firewall Configuration is Essential
A properly configured firewall acts as a security barrier between your internal network and external threats. Here’s why firewall configuration services from Elysian Communication Private Limited are crucial:
Protection Against Cyber Threats – Prevents malware, ransomware, and phishing attacks. Use strong, unique passwords:
Avoid easily guessable passwords and use a mix of uppercase and lowercase letters, numbers, and symbols.
Software and System Updates:
Keep your software and operating systems updated:
Regularly update software and operating systems to patch security vulnerabilities and protect against known exploits.
Network Security:
Secure your network:
Implement firewalls and other network security measures to protect your devices and data from unauthorized access.
Cloud Security:
Secure your cloud resources: Implement cloud security measures to protect your data and applications stored in the cloud.
Mobile Security:
Protect your mobile devices: Implement mobile security measures to safeguard your mobile devices and the data they store from unauthorized access, data breaches, and other cyber threats.
1. Network Traffic Control
Effectively manages and regulates incoming and outgoing network traffic by implementing advanced filtering mechanisms. This ensures that only legitimate and authorized data packets are allowed, preventing potential threats such as malware, unauthorized access, and bandwidth congestion. By optimizing traffic flow, businesses can maintain seamless operations and prevent network slowdowns.
2. Data Security Compliance
Ensures that all network security protocols align with industry regulations and standards, such as GDPR, HIPAA, or ISO 27001. By enforcing strict data protection policies, Firewall Configuration Services, organizations can safeguard sensitive information from breaches, unauthorized access, and cyber threats while maintaining compliance with legal and industry-specific security mandates.
3. Optimized Performance
Enhances overall network efficiency by filtering out unnecessary or malicious traffic, reducing latency, and prioritizing critical applications. Through intelligent bandwidth management and traffic shaping, organizations can ensure optimal speed, minimal disruptions, and a smooth digital experience for users, resulting in increased productivity and system reliability.
4. Remote Access Security
Provides robust protection for remote connections by implementing secure authentication protocols, VPN encryption, and multi-factor authentication (MFA). This ensures that employees, partners, and authorized personnel can securely access company resources from any location without exposing the network to cyber threats, unauthorized breaches, or data interception.
Our Firewall Configuration Services
At Elysian Communication Private Limited, Firewall Configuration Services offer a comprehensive suite of firewall services tailored to meet business security needs:
1. Firewall Installation & Setup
Our experts handle end-to-end firewall installation and setup, ensuring seamless integration with your existing network infrastructure.
2. Advanced Firewall Configuration
We customize firewall settings based on business requirements, applying access control lists (ACLs), intrusion prevention systems (IPS), and deep packet inspection (DPI).
3. Firewall Security Audits & Compliance
Regular security audits help identify vulnerabilities and ensure compliance with industry regulations like GDPR, HIPAA, and ISO 27001.
4. Real-Time Monitoring & Threat Detection
We provide 24/7 monitoring to detect and mitigate security threats before they impact business operations.
5. VPN Configuration for Secure Remote Access
Our VPN setup ensures secure access for remote employees, protecting sensitive corporate data from cyber threats.
Why is firewall configuration important?
Improper firewall configuration can result in attackers gaining unauthorized access to protected internal networks and resources. As a result, cyber criminals are constantly on the lookout for networks that have outdated software or servers and are not protected.
Why is it important to have a firewall?
Firewalls protect your computer or network from unwanted traffic coming in or going out. Firewalls can also inspect and authenticate all data packets in network traffic before they are allowed to move to a more secure environment.
Benefits of Choosing Elysian Communication Private Limited
At Elysian Communication Private Limited, Firewall Configuration Services specialize in providing top-tier firewall configuration services to ensure the highest level of network security, data protection, and performance optimization for businesses. Here’s why our services stand out:
1. Advanced Network Security
- Protects your business from malware, ransomware, phishing, and cyberattacks.
- Blocks unauthorized access and prevents security breaches.
- Implements Intrusion Prevention Systems (IPS) for real-time threat detection.
2. Intelligent Network Traffic Control
- Filters and monitors incoming and outgoing network traffic to prevent malicious activities.
- Prioritizes bandwidth for critical business applications.
- Prevents DDoS (Distributed Denial-of-Service) attacks and network congestion.
3. Compliance with Security Regulations
- Ensures adherence to industry standards such as GDPR, HIPAA, PCI-DSS, and ISO 27001.
- Implements security policies that protect sensitive business data.
- Provides compliance reports and audits for regulatory requirements.
4. Optimized Network Performance
- Enhances network speed by reducing unnecessary traffic and blocking unauthorized connections.
- Improves overall system reliability with firewall load balancing and bandwidth optimization.
- Enables faster access to essential applications and cloud-based services.
5. Secure Remote Access for Businesses
- Enables VPN (Virtual Private Network) configuration for secure work-from-home access.
- Uses Multi-Factor Authentication (MFA) to prevent unauthorized remote logins.
- Protects corporate data from cyber threats even when employees connect from different locations.
6. Real-Time Threat Monitoring & Incident Response
- 24/7 network monitoring to detect and respond to security threats immediately.
- Generates instant alerts for unusual activities to prevent data breaches.
- Provides security analytics and reporting for improved threat visibility.
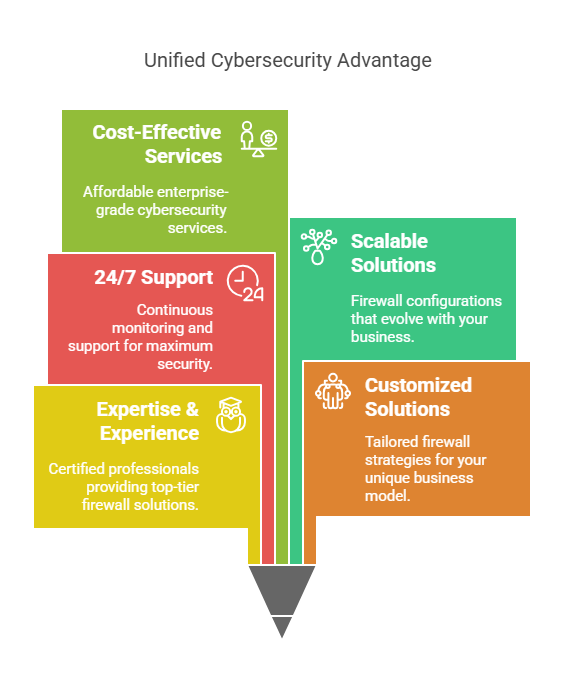
7. Cost-Effective Cybersecurity Solution
- Reduces business downtime and financial losses caused by cyberattacks.
- Minimizes IT overhead by automating firewall management and updates.
- Offers customized security solutions tailored to business needs without unnecessary expenses.
8. Scalable & Customizable Firewall Solutions
- Adapts to growing business demands with scalable firewall configurations.
- Provides custom security policies based on business size and industry requirements.
- Ensures future-proof security with regular updates and enhancements.
9. Protection Against Internal Threats
- Restricts employee access based on job roles to minimize insider threats.
- Prevents data leakage by monitoring and logging all network activities.
- Implements strict access control lists (ACLs) for sensitive information.
10. Simplified Security Management ️
- Centralized firewall management for easy rule configurations and monitoring.
- Integrates with Security Information and Event Management (SIEM) solutions.
- Reduces complexity by automating security updates and vulnerability patches.
Why Choose Elysian Communication Private Limited?
🔹 Expert Cybersecurity Team – Our certified security professionals ensure the highest level of protection.
🔹 Custom Firewall Solutions – We design industry-specific security configurations.
🔹 24/7 Monitoring & Support – Get round-the-clock network security monitoring and quick responses.
🔹 Proven Track Record – Trusted by businesses for secure and reliable firewall solutions.
Industries We Serve
Our firewall configuration services cater to diverse industries, including:
- Healthcare – Protect patient data from cyber breaches.
- Finance & Banking – Secure financial transactions and client information.
- E-commerce – Ensure a safe shopping experience for customers.
- Education – Protect student and faculty data from unauthorized access.
- Government & Public Sector – Strengthen cybersecurity in critical infrastructure.
How Our Firewall Configuration Process Works
- Assessment & Consultation – Understanding your network infrastructure and security requirements.
- Implementation & Deployment – Installing and configuring firewall solutions based on best practices.
- Testing & Optimization – Ensuring firewall effectiveness through security testing.
- Ongoing Monitoring & Maintenance – Providing continuous updates and threat monitoring.
Common Firewall Configuration Mistakes & How We Avoid Them
- Using Default Credentials – We implement strong authentication protocols.
- Ignoring Security Updates – Regular patching and firmware updates.
- Incorrect Access Control Rules – Configuring precise rules to prevent unauthorized access.
- Lack of Monitoring – Implementing real-time network traffic analysis and alerts.
1. Overly Permissive Rules:
Mistake:
Allowing too much traffic or access to resources, creating a larger attack surface.
How to Avoid:
- Implement a default-deny policy: Block all traffic by default and selectively allow only necessary traffic.
- Follow the principle of least privilege: Grant users and applications only the minimum access they need to perform their tasks.
- Regularly audit and remove unused rules: Ensure your firewall rules are up-to-date and necessary.
- Be specific and purposeful: Define rules that clearly specify the source, destination, protocol, and port for traffic.
2. Neglecting Least Privilege:
Mistake:
Granting users or applications more privileges than they need, increasing the risk of unauthorized access or actions.
How to Avoid:
- Implement least privilege: Grant users and applications only the minimum access they need to perform their tasks.
- Regularly review and adjust permissions: Ensure users and applications have the appropriate level of access.
3. Ignoring Firewall Updates:
Mistake:
Failing to update firewall firmware, software, and threat intelligence feeds, leaving the network vulnerable to known exploits.
How to Avoid:
- Regularly update your firewall: Keep your firewall software and threat intelligence feeds up-to-date.
- Patch vulnerabilities promptly: Address any known vulnerabilities as soon as possible.
4. Failing to Log and Monitor Activity:
Mistake:
Not logging firewall activity or failing to monitor logs for suspicious activity, making it difficult to detect and respond to security incidents.
How to Avoid:
- Enable logging: Ensure your firewall is logging all relevant traffic and events.
- Regularly review logs: Monitor logs for suspicious activity and potential security incidents.
- Implement intrusion detection/prevention systems: Use these systems to detect and prevent malicious activity.
5. Other Common Mistakes:
Conflicting or Obsolete Rules:
- Having rules that contradict each other or are no longer relevant can lead to unexpected behavior and security vulnerabilities.
- Misplaced or Misconfigured Devices:
- Incorrectly placing or configuring firewalls can create security gaps.
- Not Testing Your Firewall:
- Regularly testing your firewall configuration is crucial to ensure it is working as intended and to identify potential vulnerabilities.
Get Started with Elysian Communication Private Limited
If you’re looking for professional firewall configuration services, trust Elysian Communication Private Limited to deliver top-notch security solutions. Our expert team ensures that your network remains secure, efficient, and compliant with the latest cybersecurity standards.
Secure your business with our advanced firewall configuration services and stay ahead of cyber threats!





