Server Security Audit For
Resilient, Infrastructure
Ensure the integrity, confidentiality and availability of your critical systems. Server Security Audit evaluates
your servers’ security posture, identifying vulnerabilities, misconfigurations and potential threats that could
compromise your enterprise infrastructure.

KEY HIGHLIGHTS
Proactive Auditing to Secure Your Critical Infrastructure
Our Server Security Audit delivers a comprehensive assessment of your server environments to uncover hidden vulnerabilities and misconfigurations. From OS hardening and patch management to application-level security, we leave no component unchecked. We analyze access controls, firewall rules and logging mechanisms to ensure full compliance and threat resilience. By identifying gaps before they’re exploited, we help you build a fortified, stable infrastructure. Stay ahead of threats with a proactive, expert led audit that strengthens your core systems.
EXAMINE. SECURE. STRENGTHEN
Our Core Services
Analyze server configurations, patch management, and access policies for risk exposure. Ensure your critical infrastructure is hardened against known and emerging threats, and implement proactive monitoring to detect vulnerabilities in real time.
SCAN, IDENTIFY, CLEANSE
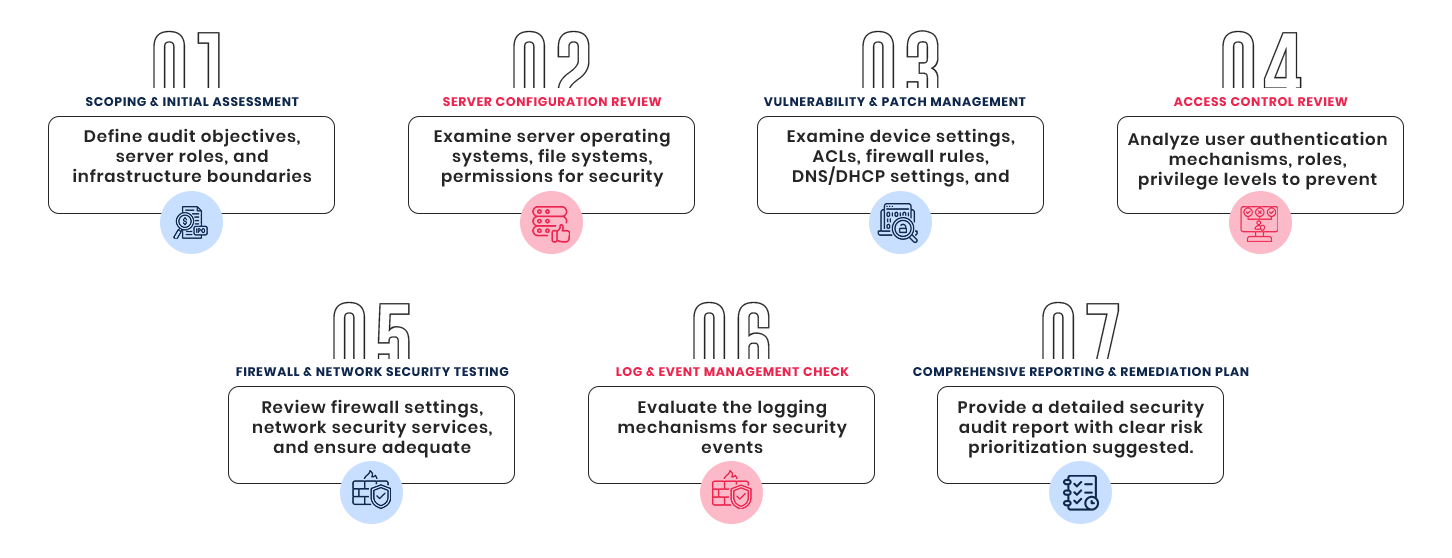
7 Stages Of Server Security Audit
Our audit follows a structured 7 stage methodology, ensuring no area of your server infrastructure goes unchecked
WHY PARTNER WITH US?
The Ultimate Defense Against Server Breaches
Our team of security experts uses cutting edge tools and methodologies to identify vulnerabilities in your servers, helping you achieve a secure and compliant environment. With us, your servers stay fortified against evolving cyber threats.

Holistic Security Approach
We assess every layer from OS settings to application configurations, ensuring your server’s security

Actionable Insights
Receive not just findings, but also actionable steps to quickly mitigate identified risks.

Comprehensive Compliance
Align your server security with industry regulations like GDPR, HIPAA, PCI-DSS and ISO 27001.
OUR PRINCIPLES AT WORK
How We Strengthen Server Security

Large Enterprise Review | Full-Scale Server Hardening
We audited over 1000 servers for a global enterprise, uncovering misconfigurations and implementing patch management to prevent breaches.

Healthcare Provider Compliance | HIPAA Security Audit
Conducted a server security audit for a healthcare provider to align with HIPAA regulations, ensuring all sensitive health data was securely handled.

Financial Institution Security | Bank-Grade Server Protection
Enhanced server security for a bank, addressing network services, encryption and access controls to safeguard against external and internal threats.
FAQ
Clear Answers To Your Cyber Security Concerns
Explore quick, expert-backed answers to common questions about our services, helping you make informed decisions and understand our approach better.
What is a Server Security Audit?
It’s a thorough examination of your server infrastructure, configurations and security measures to identify vulnerabilities and ensure compliance with industry standards.
How long does the audit take?
The timeline varies depending on the complexity of your server setup but generally ranges from a few days to a week.
Does the audit involve downtime?
No, our audits are designed to be non-disruptive, ensuring your servers remain operational throughout the process.
How is data safeguarded during penetration testing?
We audit all types of servers, including web servers, database servers, file servers, mail servers and application servers across all environments.
Will you help fix the vulnerabilities identified?
Yes, we provide a detailed remediation plan along with support in addressing any critical vulnerabilities discovered.
Is a Server Security Audit legal?
Yes, a server security audit is legal as long as it’s conducted with the authorization of the server owner and in compliance with applicable laws and regulations.









