Secure Your Digital Backbone
With Network Integrity Auditing
Ensure your entire network operates securely and efficiently. Our comprehensive Network Integrity Auditing service uncovers hidden
misconfigurations, unauthorized access points, outdated protocols and performance bottlenecks laying the foundation for a resilient,
scalable, and breach-proof infrastructure.

KEY HIGHLIGHTS
A 360° Audit For Total Network Assurance
We conduct an in-depth assessment of your network architecture, analyzing protocols, traffic patterns, and device behavior to uncover vulnerabilities and performance issues. Our evaluation helps identify misconfigurations, outdated components, and potential entry points for attackers. By aligning your infrastructure with industry security standards, we enhance both protection and efficiency. We also highlight areas for optimization to improve network resilience and reliability. The result is a secure, streamlined network that meets compliance and operational demands.
EVALUATE. FORTIFY. MITIGATE
Our Core Services
Conduct comprehensive audits to detect weaknesses in network architecture and protocols. Validate configuration, access controls, and resilience to internal and external threats.
SCAN, IDENTIFY, CLEANSE
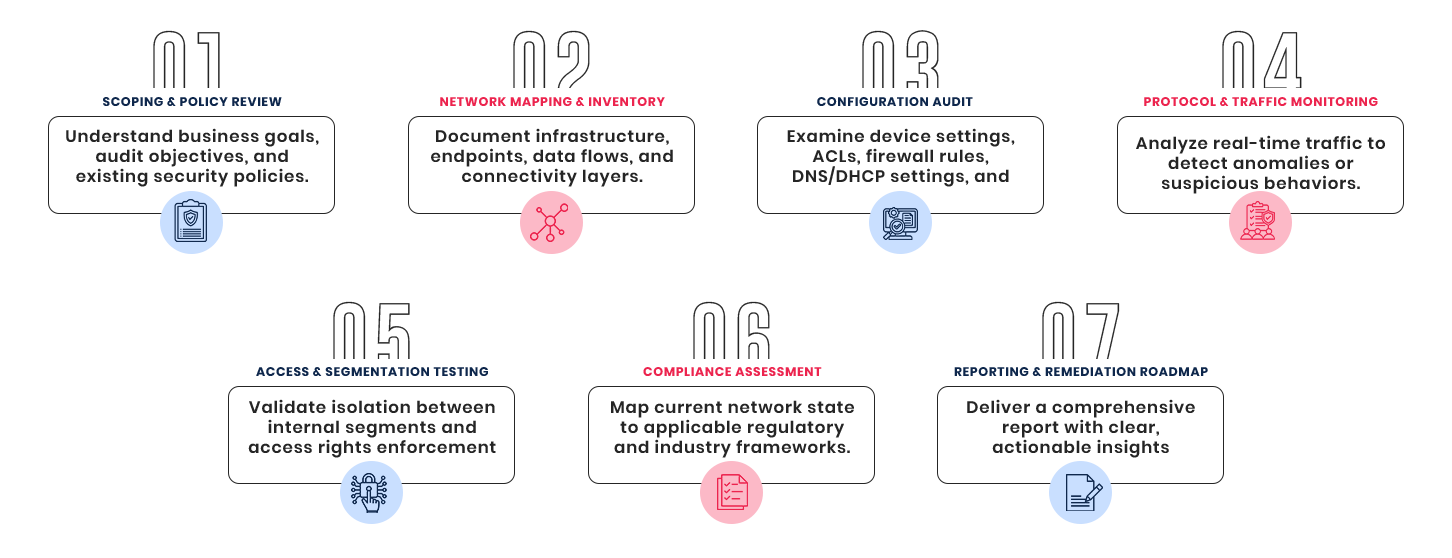
7 Stages Of Network Integrity Auditing
A wonderful serenity has taken possession of my entire soul, like these sweet mornings of spring which I enjoy with my whole heart. I am alone, and feel the charm of existence in this spot.
WHY PARTNER WITH US?
Unmatched Visibility, Unparalleled Confidence
Our Network Integrity Auditing service combines automated scanning, manual inspection, and industry-standard frameworks to provide you with full visibility into your network’s health and security.

Platform-Agnostic Expertise
Covers comprehensive hybrid, on-premise, and cloud-based networks.

Holistic & Actionable Audits
We don’t just report—we guide you to fix vulnerabilities efficiently.

Confidential & Controlled Testing
We audit without interrupting your operations, ensuring data safety throughout.
OUR PRINCIPLES AT WORK
Real Impact Through Smart Network Auditing

Global Enterprise Network Review
We helped a multinational client identify excessive open ports, outdated firmware, and undocumented connections across 6 locations.

HIPAA Alignment
Audited a healthcare provider's network to ensure HIPAA compliance and implemented access control refinements.

Secure Scalability
Assisted a tech startup in redesigning its segmented network for enhanced scalability and zero-trust implementation.
FAQ
Clear Answers To Your Cyber Security Concerns
Explore quick, expert-backed answers to common questions about our services, helping you make informed decisions and understand our approach better.
What is Network Integrity Auditing?
It’s a full-scale security and performance review of your network to ensure it is resilient, well-configured, and compliant.
What does the audit typically cover?
We assess configurations, access controls, traffic patterns, connected devices, and protocol behavior across your entire network.
Will the audit affect our live systems?
No. Our audit is designed to be non-disruptive and is carried out in a controlled, secure manner.
Who should consider this service?
Organizations with growing, complex, or regulated networks—especially those preparing for compliance audits or scaling operations.
Do you help with fixing the issues found?
Yes, we provide a prioritized remediation plan and can assist with implementation as needed.
Who should conduct a Network Integrity Audit?
Network integrity audits should be performed by certified network security professionals or third-party experts with experience in auditing and securing network systems.









