As the digital world grows more sophisticated, so do the risks that accompany it. Organizations today face relentless challenges ranging from data breaches and malware to insider threats and non-compliance penalties. Security audit services have become essential to combating these risks. Elysium Communication Private Limited, through its robust security audit solutions, helps businesses fortify their digital landscape and ensure operational continuity.
This blog explores the importance of security audit services, the specific expertise of Elysium Communication, and how network integrity auditing becomes a critical asset for any modern enterprise.
Understanding Security Audit Services
Security Audit Services are comprehensive evaluations conducted to assess the robustness, efficiency, and compliance of an organization’s IT infrastructure. In today’s data-driven environment, these audits are not optional they are a critical component of any organization’s risk management and cybersecurity strategy. By systematically analyzing IT systems, networks, protocols, access controls, and digital assets, security audit services help organizations uncover vulnerabilities that could otherwise go unnoticed until exploited.
The scope of Security Audit Services typically includes:
Network Integrity Assessments
As part of Elysium Communication Security Audit Services, network integrity assessments involve an in-depth evaluation of the performance, security, and configuration of essential hardware components such as routers, switches, endpoints, and communication protocols.

These assessments are crucial for identifying vulnerabilities that could allow unauthorized access, data leakage, or performance degradation. By ensuring all components are functioning securely and efficiently, organizations can significantly reduce their exposure to network-based threats.
Key areas of focus include:
- Physical and logical network architecture
- Configuration of routing and switching protocols
- Endpoint security measures and patch compliance
- Latency, throughput, and network bottleneck analysis
This process ensures that the entire digital infrastructure is operating in alignment with security best practices and performance expectations.
Firewall and Configuration Reviews
A misconfigured firewall can serve as an open door for cyberattacks. Elysium Communication Security Audit Services include a thorough examination of firewall settings, access control lists (ACLs), and rule sets to identify any misconfigurations or weak points.
This review focuses on:
- Analyzing inbound and outbound traffic rules
- Detecting overly permissive access policies
- Evaluating the segmentation of network zones
- Reviewing security appliances and firmware versions
By validating firewall configurations against industry standards and threat models, organizations can close critical security gaps and reinforce the perimeter of their IT environment.
Access Control Validations
One of the most common vulnerabilities in organizational networks arises from poorly managed access privileges. Elysium Communication ensures through its Security Audit Services that all user roles, access permissions, and authentication mechanisms strictly follow the principle of least privilege.
This validation process includes:
- Reviewing identity and access management (IAM) systems
- Evaluating multi-factor authentication (MFA) implementation
- Identifying privilege escalation risks
- Ensuring administrative access is limited and well-documented
Effective access control reduces the risk of insider threats and limits the impact of compromised credentials. Ensuring that users only have the access necessary for their roles is fundamental to maintaining a secure system environment.
Security Policy and Procedure Evaluations
A secure system is not only defined by technology but also by the organizational policies that govern its use. Elysium Communication Security Audit Services include comprehensive evaluations of internal security policies, procedures, and employee awareness programs.
The evaluation process involves:
- Auditing existing information security policies
- Assessing alignment with frameworks such as NIST, ISO 27001, and COBIT
- Evaluating incident response and disaster recovery procedures
- Reviewing employee onboarding and cybersecurity training protocols
This ensures that policies are not only documented but also actively enforced, measurable, and adaptable to emerging threats and regulatory requirements.
Risk Analysis and Compliance Mapping
Identifying threats and vulnerabilities and mapping controls to standards like ISO 27001, HIPAA, NIST, and GDPR. At the heart of Elysium Communication Security Audit Services is a robust risk analysis framework. This process identifies, quantifies, and prioritizes security risks across the IT infrastructure. Once risks are assessed, they are mapped to relevant compliance frameworks to ensure regulatory readiness and reduce liability.
This dual focus on risk identification and compliance ensures that organizations are both secure and legally protected. Elysium Communication provides clear, actionable insights to improve risk posture and prepare for third-party audits or certifications.
These audits do not merely provide a snapshot of current vulnerabilities they empower organizations to strengthen their entire cybersecurity posture through actionable recommendations and strategic insights.
Why Security Audits Are Crucial Today
The need for robust Security Audit Services has never been more pressing. Here’s why:
1. Protection Against Cyber Threats
The cyberthreats of today are more sophisticated, tenacious, and destructive than ever. From ransomware and phishing attacks to insider threats and zero-day vulnerabilities, organizations face a barrage of risks daily. Security Audit Services serve as a frontline defense by uncovering exploitable gaps and ensuring proactive threat mitigation. Regular audits help organizations adapt to the latest threat vectors before they cause disruption.
2. Regulatory Compliance
Various industries must comply with specific cybersecurity and data protection standards—such as ISO 27001, HIPAA, GDPR, PCI-DSS, and SOX. Failure to meet these standards can result in heavy penalties and reputational damage. Security Audit Services map existing processes and controls to the required regulatory frameworks, identifying areas of non-compliance and suggesting appropriate remediation steps. This ensures that your organization remains audit-ready at all times.
3. Business Continuity
Cyber incidents often lead to operational downtime, resulting in productivity loss, customer dissatisfaction, and financial damage. By identifying infrastructure weaknesses and potential single points of failure, Security Audit Services help businesses implement the necessary controls to avoid disruptions. A secure and resilient system is the foundation of uninterrupted business operations.
4. Client Trust and Reputation Management
In an age where data privacy and security are top priorities for customers, partners, and investors, demonstrating a strong cybersecurity framework is essential. Organizations that invest in Security Audit Services send a clear message: we take your data seriously. This not only improves stakeholder confidence but also gives you a competitive edge in the marketplace.
5. Resource Optimization
Security audits don’t just expose threats—they also reveal inefficiencies. For instance, you may find that certain systems are over-permissioned, outdated, or misaligned with your current business model. Security Audit Services highlight such redundancies and help optimize your IT resources, reducing operational costs and improving system performance. This added layer of efficiency often translates to significant long-term savings.
Network Integrity Auditing: The Elysium Communication Edge
In the increasingly digital business world, maintaining a secure and reliable network infrastructure is non-negotiable. At the core of Elysium Communication Security Audit Services lies its expertise in network integrity auditing a critical component of any comprehensive cybersecurity strategy.
This process involves a meticulous assessment of every element within a company’s digital infrastructure to identify vulnerabilities, performance issues, and configuration errors that could compromise security or disrupt operations. Elysium Communication provides a strategic advantage through its structured and results-driven auditing practices.
Core Elements of Network Integrity Auditing
Elysium Communication Security Audit Services focus on every layer of network functionality and security. Key components of network integrity auditing include:
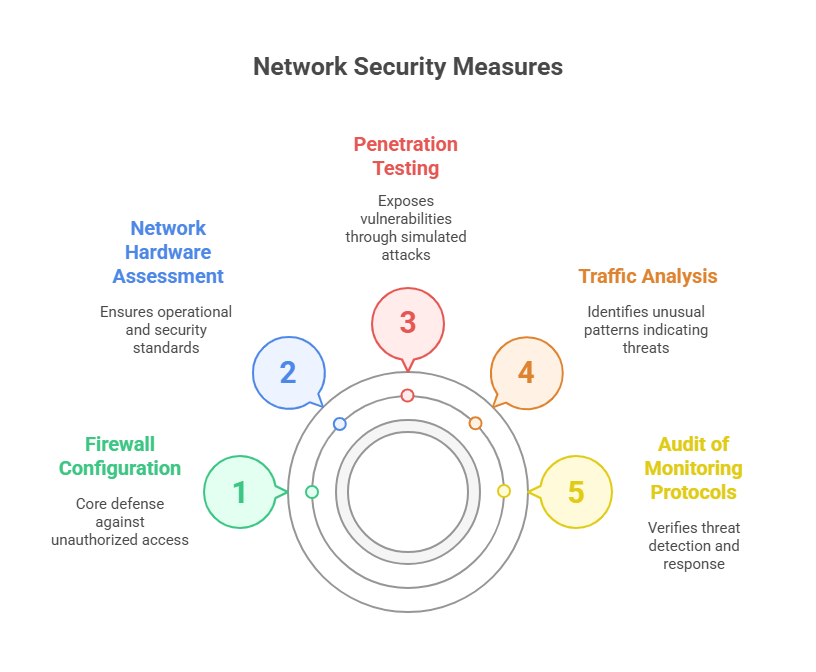
Firewall Configuration and Performance Validation: Ensures that firewall systems are optimized, updated, and configured to block unauthorized access effectively.
Assessment of Network Hardware: Routers, switches, and endpoint devices are evaluated to confirm they meet both operational and security standards.
Penetration Testing and Vulnerability Scanning: In-depth simulated attacks and automated scans are conducted to expose vulnerabilities in the network environment.
Traffic Analysis and Monitoring: Continuous monitoring identifies unusual traffic patterns that may indicate malware, data exfiltration, or other security incidents.
Audit of Monitoring Protocols: Logging systems and alerting mechanisms are reviewed to verify their capability to detect, report, and respond to threats promptly.
Through these detailed procedures, Elysium Communication delivers a comprehensive overview of an organization’s network security health and highlights both present threats and long-term infrastructure weaknesses.
Security Audit Methodology at Elysium Communication
Elysium Communication implements a multi-stage approach to deliver Security Audit Services that are both thorough and adaptable to diverse industry needs. Each audit is customized to align with the client’s objectives, regulatory requirements, and business environment.
1. Discovery and Requirement Analysis
This phase involves understanding the client’s IT landscape and security objectives. Critical systems, data assets, and business priorities are identified to set the foundation for the audit.
2. Risk Profiling
Security risks—both internal and external—are evaluated based on the organization’s existing infrastructure. This includes a review of historical incidents, threat intelligence data, and current exposure points.
3. Technical Assessment
Automated scanning tools are employed to identify vulnerabilities quickly, while manual testing techniques target high-risk areas for a deeper analysis. This hybrid method ensures no weakness is overlooked.
4. Configuration and Access Reviews
A complete review of access management is conducted. This includes analysis of user roles, permissions, firewall rules, endpoint protection mechanisms, and segmentation practices.
5. Compliance Mapping
Systems and policies are evaluated against leading compliance standards such as ISO 27001, GDPR, NIST, CIS, and PCI-DSS. Recommendations are made to bridge any compliance gaps and prepare the organization for formal certification or audits.
6. Reporting and Documentation
A detailed audit report is generated, categorizing vulnerabilities by severity and impact. Actionable insights are provided for both immediate remediation and long-term improvements.
7. Remediation Support and Retesting
Post-audit support includes guidance for implementing security enhancements. Once changes are applied, a follow-up assessment is performed to ensure all vulnerabilities have been effectively addressed.
Benefits of Elysium Communication Security Audit Services
Partnering with Elysium Communication offers organizations unparalleled access to best-in-class Security Audit Services. Key benefits include:
Comprehensive Risk Identification
One of the defining strengths of Elysium Communication Security Audit Services is the ability to perform multi-layered risk assessments. Unlike traditional audits that only scratch the surface, Elysium’s audits dig deep into your organization’s infrastructure—identifying both superficial vulnerabilities and deep-rooted systemic weaknesses that could compromise your security posture.
Our team evaluates physical, technical, and administrative controls to uncover overlooked security weaknesses. Risks are assessed based on severity, exploitability, and business impact. This deep analysis helps develop strategic mitigation plans tailored to your operational needs.
Tailored Audit Programs
Elysium Communication understands that no two organizations are alike, and a one-size-fits-all approach to cybersecurity auditing is ineffective. That’s why its Security Audit Services are designed to be fully customizable based on your business’s size, structure, and industry regulations.
We begin with an in-depth consultation to align audit parameters with business objectives. Industry-specific regulatory obligations are incorporated directly into the auditing framework. The result is a personalized audit roadmap that delivers maximum relevance and actionable insights.
Expertise You Can Trust
With a team composed of certified cybersecurity professionals, Elysium Communication brings decades of combined experience to every engagement. Its Security Audit Services are guided by real-world expertise, informed by current threat intelligence, and grounded in the best practices of international cybersecurity frameworks.
We have successfully audited complex IT ecosystems across government, enterprise, and SME environments. Our experts hold certifications such as CISSP, CEH, ISO Lead Auditor, and more. This foundation allows us to deliver audits with both precision and strategic foresight.
Advanced Audit Tools
To ensure maximum coverage and precision, Elysium Communication integrates both automated scanning tools and manual testing techniques within its Security Audit Services. This dual approach ensures that vulnerabilities are detected regardless of their nature whether they’re obvious misconfigurations or subtle zero-day threats.
Our tools are chosen for their accuracy, depth, and compliance with global cybersecurity standards. Manual validation ensures that context-specific risks are accurately interpreted. This hybrid method bridges the gap between automation efficiency and human judgment.
Early Threat Detection
Proactive threat identification is a critical advantage of Elysium Communication Security Audit Services. The ability to detect vulnerabilities before they are exploited enables organizations to implement timely defenses and avoid potentially devastating incidents.
Early detection reduces potential attack surfaces and increases response readiness. Our proactive strategies help organizations stay ahead of threat actors by anticipating their methods. This ultimately leads to improved uptime, business continuity, and customer trust.
End-to-End Service Delivery
Security is not a one-time task—it is a continuous process. That’s why Elysium Communication provides end-to-end support as part of its comprehensive Security Audit Services. From the first consultation to final verification, the process is carefully managed to ensure complete visibility, accountability, and support.
Clients benefit from a fully managed audit lifecycle that includes guidance at every stage. We offer hands-on remediation support to ensure implementation accuracy. Post-remediation testing verifies the effectiveness of solutions and closes the loop on all findings.
Industries Served by Elysium Communication
Elysium Communication Security Audit Services are designed to accommodate the unique regulatory and operational demands of various sectors. Whether your organization is part of a tightly regulated industry or an emerging field, Elysium offers the right level of precision and expertise.
- Healthcare: Protection of electronic health records (EHRs) and HIPAA compliance support.
- Banking and Financial Services: Ensuring data security for transactions and adherence to PCI-DSS standards.
- Education: Safeguarding student data, academic records, and IT infrastructure.
- Retail and E-commerce: Protection for customer information, payment systems, and digital storefronts.
- Telecommunications: Securing communication systems, backend operations, and user data transmission.
Elysium Communication crafts specialized audit strategies for each industry to ensure compliance, resilience, and peace of mind.
Future-Proofing Security with Elysium Communication
The role of Security Audit Services extends beyond resolving current vulnerabilities. Elysium Communication emphasizes a proactive approach that incorporates advanced technologies and forward-looking strategies:
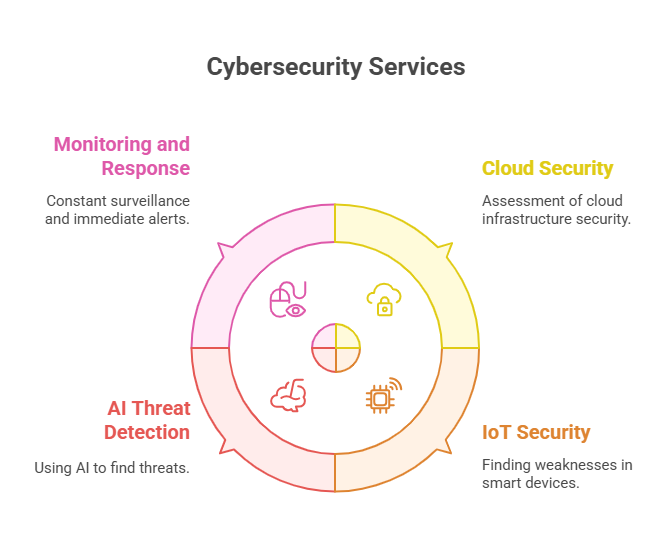
- Cloud Security Audits: Secure assessment of infrastructure on cloud platforms like AWS, Microsoft Azure, and Google Cloud.
- IoT Security Evaluations: Identification of vulnerabilities in smart and connected devices increasingly used across industries.
- AI-Driven Threat Detection: Integration of artificial intelligence and machine learning for predictive and real-time threat analysis.
- Continuous Monitoring and Response: Implementation of systems that allow round-the-clock surveillance and instant alerts for suspicious activity.
These innovations position Elysium clients ahead of the threat curve, ready to handle both present-day risks and future challenges.
Why Choose Elysium Communication for Security Audit Services?
Selecting the right partner for Security Audit Services is vital for building a resilient security framework. Elysium Communication distinguishes itself through a commitment to quality, trust, and client-focused service:
- Extensive Experience: Over a decade of service in delivering cybersecurity solutions across industries
- Full-Cycle Audit Services: Covering everything from pre-audit consultation to final retesting and support
- Confidentiality and Integrity: Client information is handled with the highest level of security and discretion
- Scalable and Flexible Delivery: Whether you’re a small business or a multinational enterprise, Elysium adapts its services to meet your needs
- Continuous Learning and Improvement: The audit team is constantly trained on the latest security trends, threats, and compliance mandates
Investing in Security Audit Services by Elysium Communication is more than a defensive measure it’s a strategic move toward business continuity, trust, and digital transformation. With a clear understanding of your current security posture, expert recommendations, and support for remediation, your organization can confidently face today’s threats and prepare for tomorrow’s challenges.
Conclusion
The rising tide of cyber threats means organizations must be proactive rather than reactive. Security audit services, particularly those offered by seasoned experts like Elysium Communication Private Limited, help companies build a solid security foundation. By identifying weaknesses, ensuring compliance, and mitigating risk, these audits safeguard business continuity and stakeholder trust.
Elysium Communication network integrity auditing goes beyond surface-level analysis to deliver in-depth, actionable results. With its strategic approach, industry expertise, and commitment to excellence, Elysium Communication stands out as a reliable partner for your organization’s digital defense. Secure your systems today, for a safer tomorrow.
Frequently Asked Questions (FAQs)
1. What makes Elysium Communication Private Limited a trusted name in security audit services?
Elysium Communication offers end-to-end solutions with in-depth technical expertise and a proactive security approach. With a focus on network integrity auditing and regulatory compliance, we ensure reliable outcomes and long-term value.
2. Does Elysium Communication provide post-audit support and implementation assistance?
Yes. Clients receive detailed remediation guidance along with hands-on assistance to fix vulnerabilities. Follow-up audits and employee training sessions are also available.
3. Can startups and SMEs afford your security audit services?
Absolutely. Our service packages are scalable and customizable, making them accessible for businesses of all sizes without compromising quality.
4. How often should businesses conduct a security audit?
At a minimum, once a year. However, audits should also be performed after significant changes in infrastructure, following a breach, or before compliance deadlines.
5. Do your audits cover hybrid and cloud-based systems?
Yes. Our audits include comprehensive evaluations of hybrid infrastructures, cloud services, and remote access configurations, ensuring complete coverage.





