In today’s highly connected digital world, malicious software, commonly called malware, has emerged as one of the most persistent and expensive threats facing organizations of every size. Whether it’s a small business or a global corporation, no organization is completely safe from the risk of cyber compromise. Malware analysis plays a crucial role in identifying, understanding, and neutralizing these threats before they can inflict irreparable damage.
Consider the 2024 breach of a major logistics company, where a cleverly disguised ransomware variant shut down operations for days. Cybercriminals used an innocent-looking email attachment as a delivery method to deploy malware, which ultimately locked down essential databases through encryption. It wasn’t until cybersecurity experts conducted a detailed malware analysis that they uncovered the payload’s delivery method, decryption mechanism, and network communication patterns—ultimately leading to a recovery plan and improved defenses.
This example underscores a critical truth: understanding malware behavior is just as important as detecting its presence.
Malware Analysis
Simply put, malware analysis is the practice of investigating malicious programs to understand their source, behavior, and potential consequences on affected systems. It’s like digital forensics for harmful code—pulling apart its structure and monitoring its behavior to understand what it’s designed to do.
The primary goals of malware analysis include:
- Detection: Confirm whether a suspicious file, process, or network activity is actually malicious.
- Behavior Understanding: Uncover how the malware functions, spreads, and interacts with systems and networks.
- Response Enablement: Deliver actionable intelligence to swiftly contain, eradicate, and prevent the threat from reoccurring.
The sophistication of malware has evolved dramatically. Attackers now employ encryption, polymorphism, fileless execution, and other evasive techniques. This has made malware analysis not just a helpful skill but a necessity for effective cybersecurity.
Key Phases of a Malware Investigation

A professional malware investigation follows a structured, methodical process to ensure nothing is missed and all findings are accurate.
a. Collection & Initial Assessment
The first step in any malware analysis is identifying suspicious files or unusual activity. This can happen via:
- Automated Detection: Alerts from endpoint detection systems (EDR) or SIEM tools.
- Honeypots: Decoy systems intentionally designed to lure malware.
- User Reports: Employees flagging unusual system behavior.
Samples may arrive as suspicious executables, macros, scripts, or even memory dumps.
b. Documentation & Chain of Custody
Proper logging is vital. From the moment a sample is acquired, analysts document:
- Date and time of collection.
- Source of the sample.
- File hashes (MD5, SHA-256).
- Initial observations.
Maintaining a strict chain of custody ensures that findings from the malware analysis can be trusted, and in some cases, used as legal evidence.
c. Static Analysis (Non-Execution Examination)
In this phase, the malware is analyzed without executing it on any system. Analysts may:
- Review file headers, structure, and size.
- Extract embedded resources like images or strings.
- Identify imports and exports in executables.
- Check against known malware signatures.
Hashing samples and comparing them to threat intelligence databases allows for quick identification, while suspicious strings can hint at command-and-control domains or targeted systems.
d. Dynamic (Behavioral) Analysis
Dynamic analysis entails running the malware within a secure, isolated environment to observe its behavior in real time:
- System Changes: New files, altered registry keys, or modified system libraries.
- Network Traffic: Outbound connections, data exfiltration attempts, or beaconing to C2 servers.
- Process Monitoring: Creation of hidden processes, injection into legitimate processes, or persistence creation.
Behavioral insights are among the most valuable outcomes of malware analysis, helping analysts understand not only what the malware is but what it does in real-world conditions.
e. Code Analysis & Reverse Engineering
For sophisticated or highly obfuscated malware, reverse engineering becomes necessary:
- Using disassemblers (like IDA Pro or Ghidra) to read assembly code.
- Debugging the malware to step through its instructions.
- Unpacking encrypted or compressed sections to reveal hidden logic.
This phase is where experts discover persistence methods, encryption algorithms, and even mistakes left by attackers that can be exploited for defense.
f. Impact Assessment
Once the behavior is understood, the impact must be evaluated:
- Which systems or users were affected?
- Was sensitive data accessed or stolen?
- Did the malware spread laterally across the network?
Malware analysis findings in this stage directly inform the recovery plan and communication strategy.
g. Artifact and IOC Extraction
Indicators of compromise (IOCs) play a vital role in detecting threats across an entire organization:
- File hashes.
- Malicious domains or IP addresses.
- Registry entries or mutexes.
These artifacts enable security teams to scan systems, identify any remaining infections, and prevent future attacks.
h. Reporting & Recommendations
A well-structured report includes:
- A narrative of the attack chain.
- Detailed technical findings.
- Remediation guidance.
The reporting phase ensures that insights from malware analysis translate into actionable security improvements.
Why Is Malware Analysis Vital for Organizations?
The benefits of investing in malware analysis extend far beyond a single incident:
- Rapid Isolation: Contain threats quickly to limit damage.
- Enhanced Readiness: Leverage insights gained from incidents to strengthen defenses and prepare for potential future attacks.
- Security Maturity: Continuous improvement of detection and response capabilities.
Without proper analysis, organizations risk repeated infections, hidden backdoors, and unaddressed vulnerabilities.
Common Types of Malware Investigated
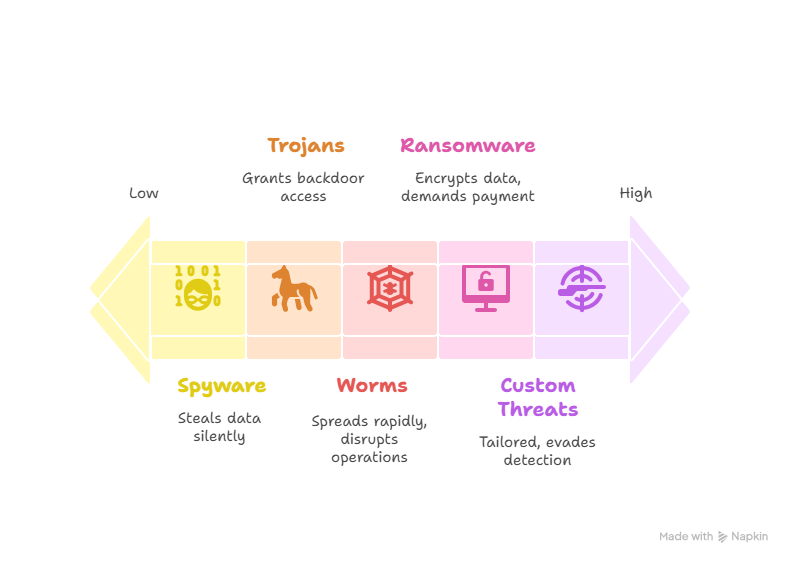
1. Ransomware
Ransomware is malware that locks a victim’s files or entire system through encryption, making them inaccessible until a ransom is paid. The attackers typically demand a ransom—frequently in cryptocurrency—in return for the key to decrypt the affected files.
- Example: A hospital’s patient database is locked by ransomware, forcing operations to halt until either the ransom is paid or backups are restored.
- Why it’s dangerous: It can cause massive business downtime, financial loss, and reputational damage.
2. Trojans
Trojans are malicious programs that appear to be legitimate software, aiming to deceive users into installing them. Once inside, they create “backdoors” that allow attackers to remotely control the system.
- Example: A fake PDF reader installer that, once downloaded, gives hackers access to corporate email systems.
- Why it’s dangerous: They can bypass defenses by exploiting user trust and deliver other forms of malware.
3. Spyware
Spyware covertly tracks and gathers user data without their knowledge or permission. It can capture keystrokes, screen activity, and browser history.
- Example: A piece of spyware records every keystroke entered on an e-commerce site, stealing credit card details.
- Why it’s dangerous: It compromises sensitive data, leading to identity theft or corporate espionage.
4. Worms
Worms are malware that automatically replicate and spread across networks without requiring any user interaction. They often exploit security vulnerabilities to propagate.
- Example: A worm enters through an unpatched server and spreads to all connected devices, slowing operations and installing additional payloads.
- Why it’s dangerous: They can quickly infect entire networks, causing widespread operational disruption.
5. Custom Threats
Custom threats are malware variants specifically designed for a targeted organization, industry, or system. They are frequently able to bypass conventional security measures and remain undetected.
- Example: Malware engineered to steal blueprints from a manufacturing company’s proprietary design software.
- Why it’s dangerous: Tailored attacks are harder to detect, and their unique nature means existing defenses may not recognize them.
How Elysian Communication Can Help
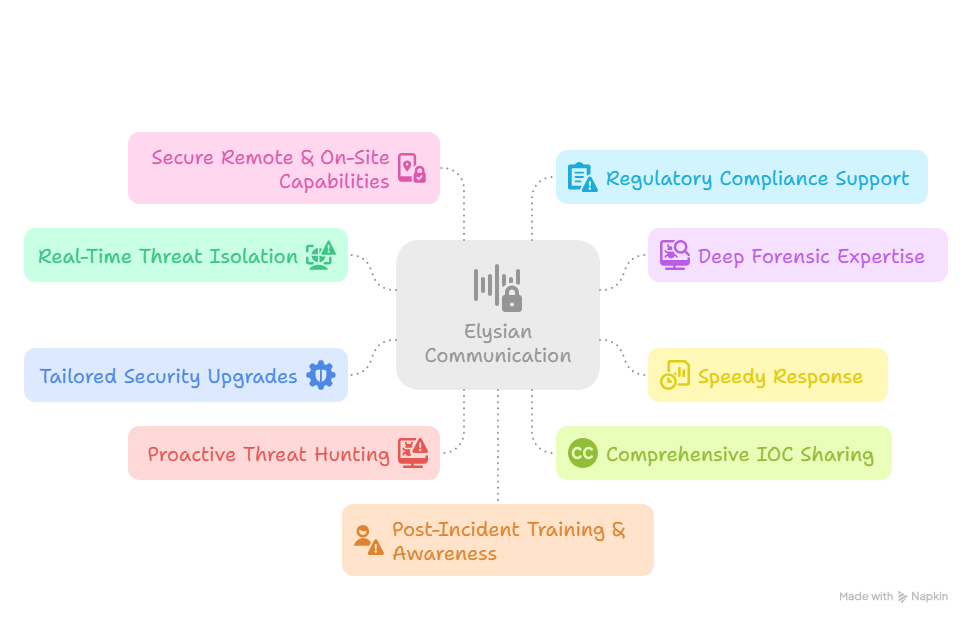
Elysian Communication specializes in rapid, expert-led malware analysis for businesses across all industries. We combine advanced tools, experienced professionals, and proven processes to detect, dissect, and defend against even the most sophisticated cyber threats.
1. Real-Time Threat Isolation
We swiftly isolate active threats as soon as they are identified. This rapid response prevents the malware from spreading, minimizing damage to your systems and data.
- Benefit: Reduces downtime and prevents further compromise while investigation is underway.
2. Deep Forensic Expertise
Our team includes skilled reverse engineers and malware analysts who uncover even the most hidden, obfuscated, or encrypted malware functions.
- Benefit: Enables us to fully understand the threat’s purpose, persistence methods, and weaknesses for complete eradication.
3. Speedy Response
We prioritize efficiency without compromising accuracy. Our streamlined triage process allows us to start analysis within hours of engagement.
- Benefit: Enables businesses to return to normal operations quickly with minimal downtime.
4. Tailored Security Upgrades
Post-analysis, we recommend customized security improvements based on your organization’s environment and the specific attack vector used.
- Benefit: Strengthens your defenses against similar threats in the future.
5. Proactive Threat Hunting
We don’t just wait for alerts—we actively search for hidden malware, compromised accounts, or unusual activity within your network.
- Benefit: Identifies dormant threats before they activate, preventing future incidents.
6. Comprehensive IOC Sharing
We extract and share detailed Indicators of Compromise (IOCs)—such as malicious file hashes, IPs, and registry keys—with your security team.
- Benefit: Enhances your internal monitoring systems and enables faster detection of repeat attempts.
7. Secure Remote & On-Site Capabilities
Whether you require immediate remote assistance or on-site forensic investigation, our team adapts to your needs.
- Benefit: Ensures quick engagement regardless of your location or infrastructure setup.
8. Regulatory Compliance Support
We help you document incidents in a way that meets industry compliance standards (ISO 27001, GDPR, HIPAA, etc.).
- Benefit: Reduces legal risks and ensures audit readiness after a breach.
9. Post-Incident Training & Awareness
We provide targeted training to IT teams and employees based on the lessons learned from the incident.
- Benefit: Builds a human firewall by reducing the risk of user-triggered infections.
FAQs
1. Can malware analysis be done remotely?
Yes. Secure transfer and sandbox execution allow for remote investigation without exposing your systems.
2. How long does malware analysis take?
It depends on complexity—simple cases may take hours, advanced threats could require days or weeks.
3. Will you help with recovery?
Certainly. After completing the analysis, we provide support with containment, removal, and measures to prevent future attacks.
4. Is my data safe during analysis?
Yes. All work is conducted in isolated, secure environments with strict confidentiality protocols.
Conclusion
The continuously changing cyber threat environment requires a proactive and vigilant approach to defense. Malware analysis is not just an optional skill—it’s a cornerstone of modern cybersecurity. By understanding how malware operates, organizations can respond quickly, recover efficiently, and harden their defenses against future attacks.
In a world where a single unnoticed infection can lead to catastrophic data loss or reputational harm, expert-led malware investigation is your best safeguard.
Don’t wait until it’s too late. If you suspect suspicious activity or have experienced a cyber incident, contact Elysian Communication today. Our malware analysis experts are ready to detect, dissect, and defend against modern threats—keeping your business secure and resilient.





