Threat Exposure Analysis helps organizations uncover hidden vulnerabilities, prioritize risks, and build stronger cybersecurity defenses. Learn why it matters and how Elysian Communication can protect your business.
Why Threat Exposure Analysis Matters Now
Each day, cyber threats are becoming increasingly advanced and complex. From ransomware to phishing and advanced persistent threats (APTs), organizations face relentless risks that can disrupt operations, erode customer trust, and cause financial losses. Traditional approaches like periodic vulnerability scans or basic firewalls are no longer enough.
This is where Threat Exposure Analysis (TEA) comes into play. Unlike one-time checks, it provides a holistic, continuous view of your organization’s attack surface, uncovering risks before attackers exploit them. By proactively addressing exposures, businesses can stay ahead of cybercriminals while strengthening compliance and resilience.
What Is Threat Exposure Analysis?
Threat Exposure Analysis (TEA) is an advanced cybersecurity approach that surpasses conventional vulnerability assessments. While vulnerability scans only highlight known software flaws, TEA provides a 360-degree view of an organization’s security posture, focusing on the entire attack surface—the places where attackers could potentially break in.
Think of it as a health check-up for your IT ecosystem. Instead of checking just one symptom, it looks at all possible weak points that might expose your organization to real-world threats.
Here’s what TEA covers in detail:
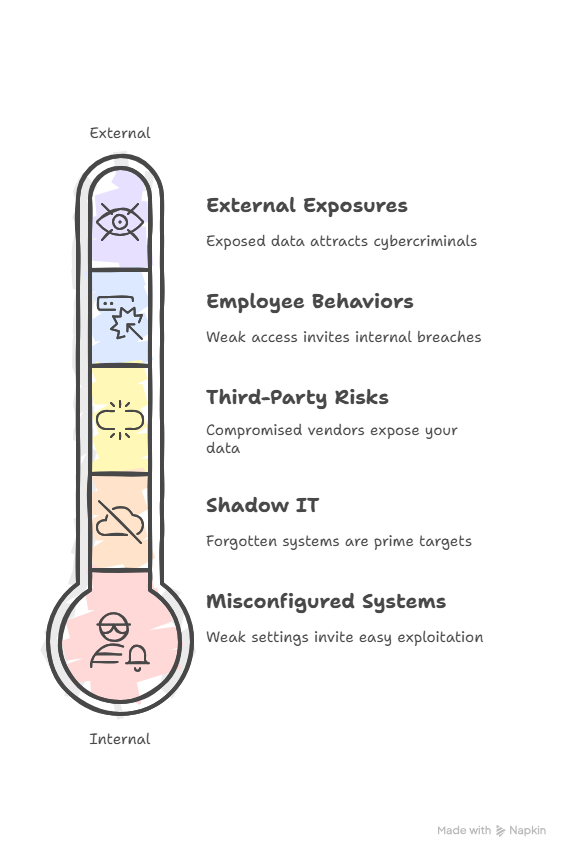
- Misconfigured Systems and Endpoints
- A single weakly configured server, database, or endpoint can open the door to hackers.
- For example, leaving default admin passwords unchanged or failing to update firewalls can create massive risks.
- TEA identifies these weaknesses and recommends fixes before they’re exploited.
- A single weakly configured server, database, or endpoint can open the door to hackers.
- Shadow IT Assets (Unknown or Forgotten Systems)
- Many organizations have unmonitored devices, old servers, or unused applications still connected to their networks.
- Hackers love these “forgotten” systems because no one is watching them.
- TEA shines a light on these blind spots, ensuring every asset is accounted for.
- Many organizations have unmonitored devices, old servers, or unused applications still connected to their networks.
- Third-Party Integrations and Supply Chain Risks
- Today’s businesses depend heavily on vendors, cloud services, and software integrations.
- If a third-party system is compromised, your organization may also be exposed.
- TEA evaluates these external connections to reduce supply chain vulnerabilities.
- Today’s businesses depend heavily on vendors, cloud services, and software integrations.
- Employee Behaviors and Weak Access Controls
- Mistakes made by individuals continue to be among the leading risks in cybersecurity.
- Weak passwords, shared credentials, or excessive user privileges make it easier for attackers to infiltrate systems.
- TEA helps assess and strengthen policies like multi-factor authentication (MFA) and role-based access.
- Mistakes made by individuals continue to be among the leading risks in cybersecurity.
- External Exposures Visible to Attackers
- Cybercriminals often scan the internet for exposed servers, open ports, or leaked credentials.
- TEA simulates this attacker’s perspective, identifying what outsiders can “see” about your organization online.
- Cybercriminals often scan the internet for exposed servers, open ports, or leaked credentials.
Threat Exposure vs. Vulnerability Management: Explained
Many organizations assume vulnerability management is enough to protect them. While it’s an essential security practice, it’s only one piece of the puzzle. Threat Exposure Analysis (TEA) takes things further by looking at the entire risk landscape instead of just patching software bugs.
Here’s the comparison explained point by point:
1. Focus: Known Software Flaws vs. Entire Attack Surface
- Vulnerability Management:
Focuses mainly on software flaws—bugs in applications, operating systems, or databases that can be patched.
Example: Running a scan to detect outdated software versions. - Threat Exposure Analysis:
Looks at the entire attack surface, which includes not just software bugs, but also:
- Misconfigured firewalls or servers
- Employee mistakes (weak passwords, sharing accounts)
- Forgotten assets (old servers still online)
- Third-party vendor risks
This gives a broader and more realistic picture of how attackers might break in.
- Misconfigured firewalls or servers
2. Timing: Point-in-Time vs. Continuous Monitoring
- Vulnerability Management:
Usually done periodically (monthly, quarterly, or annually). Risks that emerge between scans often remain undetected until the next cycle. - Threat Exposure Analysis:
Involves continuous, dynamic monitoring. It tracks your digital environment in real-time, alerting you immediately when new exposures or misconfigurations appear.
3. Approach: Reactive vs. Proactive
- Vulnerability Management:
A reactive process—you find flaws and fix them. It’s like plugging leaks in a boat after water starts seeping in. - Threat Exposure Analysis:
A proactive process—it identifies risks most likely to be exploited and addresses them before attackers act. This enables security teams to maintain a proactive edge.
4. Context: Limited vs. Business-Aligned
- Vulnerability Management:
Often provides raw lists of vulnerabilities without context. IT teams may waste time fixing minor issues while ignoring more serious risks. - Threat Exposure Analysis:
Is context-driven. It considers:
- Which assets are critical for business operations
- What vulnerabilities are currently being targeted and exploited in real-world environments?
- What the impact would be if a system is compromised
This ensures that efforts are aligned with business priorities, not just technical fixes.
- Which assets are critical for business operations
Core Components of Threat Exposure Analysis
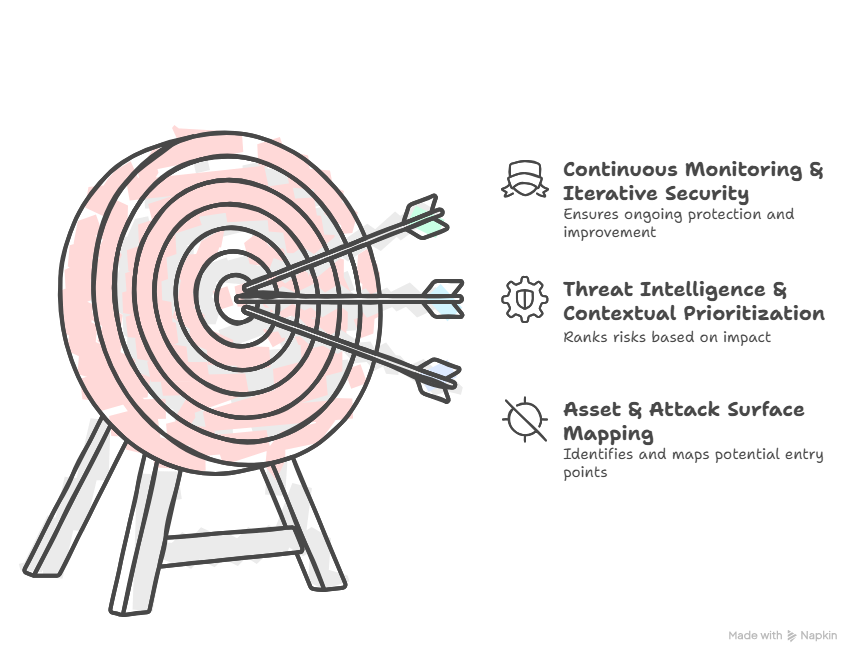
A strong Threat Exposure Analysis (TEA) framework is not a one-time checklist—it is an ongoing, layered approach. Each layer provides critical visibility and intelligence to help organizations reduce their risk exposure and prevent cyberattacks.
1. Asset & Attack Surface Mapping
It’s impossible to safeguard assets you aren’t aware of. Most organizations have more digital assets online than they realize, including servers, applications, cloud services, IoT devices, and even forgotten systems. Each of these can serve as a potential entry point for attackers.
Key functions:
- Identifies shadow IT (unauthorized or unmanaged devices/software)
- Detects abandoned assets still exposed to the internet
- Maps pathways attackers could exploit to access critical systems
Example: A business may move to a new cloud server but forget to decommission the old one. TEA detects the unmonitored server before it becomes a target for hackers.
2. Threat Intelligence & Contextual Prioritization
Each vulnerability poses a different degree of risk and impact. Some flaws are actively exploited in the wild, while others may have little to no impact. Without prioritization, businesses risk wasting resources on low-level issues while ignoring critical threats.
Key functions:
- Links vulnerabilities to known attack campaigns through threat intelligence feeds
- Ranks risks based on potential business impact
- Helps security teams allocate resources effectively
Example: Two servers may be vulnerable, but only one holds sensitive customer data. TEA ensures the more critical server is addressed first.
3. Continuous Monitoring & Iterative Security
Cyber risks evolve daily. A system that is secure today can become vulnerable tomorrow due to new exploits, misconfigurations, or software updates. One-time scans are not sufficient.
Key functions:
- Detects new misconfigurations and vulnerabilities as they appear
- Provides ongoing remediation guidance rather than static reports
- Establishes a continuous cycle of improvement, ensuring long-term resilience
Example: If cloud storage settings are accidentally changed to allow public access, TEA immediately detects the exposure, preventing attackers from exploiting it.
Why Proactive Threat Exposure Analysis Wins
Organizations that adopt TEA gain multiple advantages:
Early Detection Prevents Disasters
Catching exposures early prevents data breaches, ransomware infections, and downtime. By the time attackers exploit a weakness, it’s often too late—proactive analysis keeps businesses ahead.
Prioritization Conserves Resources
Cybersecurity budgets are limited. TEA ensures companies focus on the highest-priority risks instead of spreading resources too thin.
Enhanced Governance & Stakeholder Clarity
At Elysian Communication, we emphasize a proactive and transparent approach to cybersecurity that aligns seamlessly with your business goals. TEA translates findings into business-relevant insights, aligning IT with compliance and governance.
Why Choose Elysian Communication for Threat Exposure Analysis
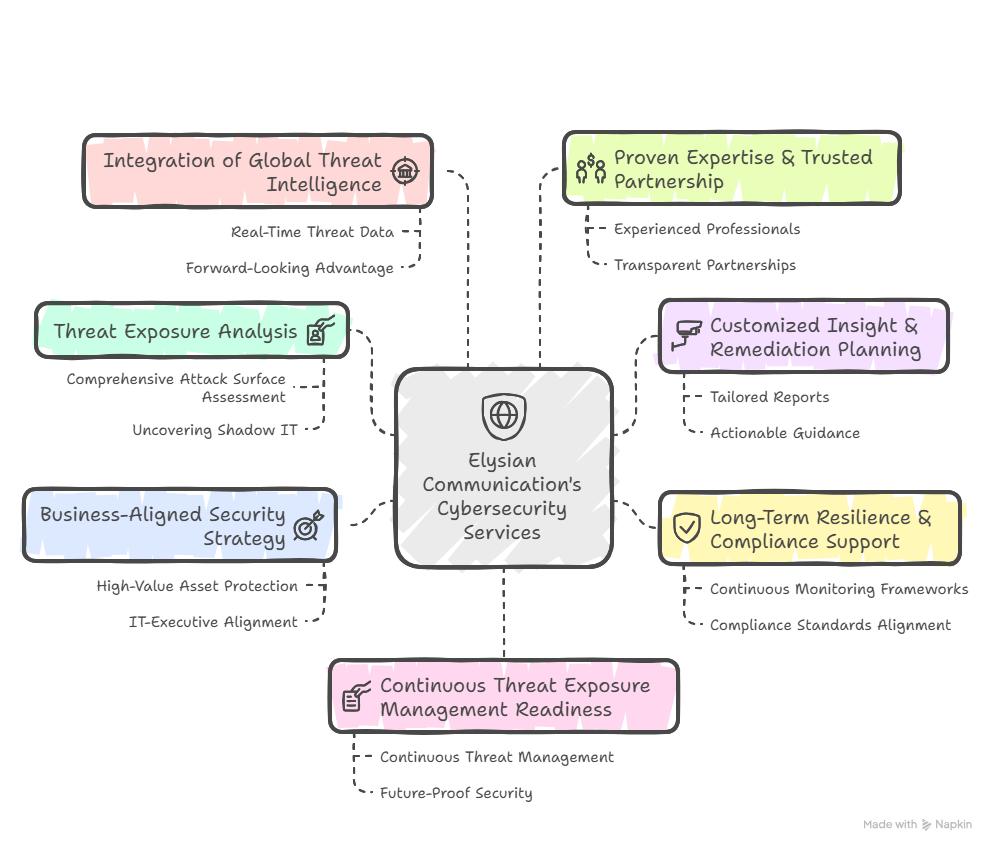
At Elysian Communication, we view cybersecurity as a proactive and transparent practice designed to align perfectly with your organization’s strategic objectives. Our Threat Exposure Analysis (TEA) service goes beyond traditional security checks, offering organizations unparalleled visibility, prioritized insights, and long-term resilience.
Here’s why businesses trust us:
Comprehensive Attack Surface Assessment
We use advanced scanning tools, automation, and expert analysis to map every corner of your digital environment—including on-premises infrastructure, cloud assets, APIs, and third-party connections. By uncovering shadow IT and abandoned assets, we eliminate hidden risks before attackers can exploit them.
Customized Insight & Remediation Planning
No two organizations are the same. That’s why our team delivers tailored reports with clear, prioritized remediation steps. Instead of overwhelming you with technical jargon, we provide actionable guidance that strengthens security without disrupting operations.
Long-Term Resilience & Compliance Support
Cybersecurity is not a one-time project. We partner with organizations to establish continuous monitoring frameworks, ensuring defenses adapt as threats evolve. We also help align with key compliance standards such as ISO, GDPR, and PCI-DSS, reducing audit stress and regulatory risk.
Business-Aligned Security Strategy
We don’t just focus on technology—we align our analysis with your business priorities. This ensures that high-value assets, like customer databases or financial systems, are given the highest protection. Our methodology closes the gap between IT departments and executive leadership.
Integration of Global Threat Intelligence
We enrich our analysis with real-time global threat intelligence, highlighting exposures that attackers are actively exploiting worldwide. This gives you a forward-looking advantage in tackling the most pressing risks first.
Proven Expertise & Trusted Partnership
Our cybersecurity professionals bring deep expertise in managing exposures, analyzing vulnerabilities, and responding effectively to incidents. Clients choose us not just for our technical capabilities but also for our commitment to building transparent, long-term partnerships.
Continuous Threat Exposure Management (CTEM) Readiness
We prepare businesses for the future of security by incorporating continuous threat exposure management principles—ensuring your organization stays one step ahead in an ever-changing digital landscape.
FAQs
1. What is Threat Exposure Analysis in simple terms?
It’s a proactive process to uncover hidden risks across your IT environment before attackers exploit them.
2. How is it different from vulnerability scanning?
Vulnerability scanning finds flaws in software; TEA covers the entire attack surface including misconfigurations, third-party risks, and human factors.
3. How often should organizations run TEA?
Ideally, Threat Exposure Analysis should function as an ongoing practice rather than a single audit.
4. Does TEA help with compliance?
Absolutely. TEA aids in adhering to standards such as ISO, GDPR, and PCI-DSS by minimizing risks and ensuring audit preparedness.
5. Is TEA only for large enterprises?
No. Small and medium businesses also benefit—cybercriminals increasingly target them due to weaker defenses.
Conclusion: The Future Belongs to the Proactive
The digital battlefield is constantly shifting. Companies that rely on outdated, reactive strategies are at a severe disadvantage. Threat Exposure Analysis goes beyond being a security measure—it serves as a catalyst for business growth.
By identifying, prioritizing, and mitigating risks, TEA helps organizations protect data, ensure compliance, conserve resources, and build trust with stakeholders.
At Elysian Communication, we help businesses shine a light on hidden risks and transform cybersecurity into a driver of resilience and growth.
👉 Ready to uncover your hidden vulnerabilities?
Visit Threat Exposure Analysis – Elysian Communication and take the first step towards a safer digital future.




