Malware investigation, also known as malware analysis, is the process of examining malicious software to understand its functionality, origin, and impact. This involves using techniques like static analysis and dynamic analysis (running the code in a controlled environment) to gather intelligence for defending against and mitigating future threats. The goal is to develop defenses, create threat intelligence, and understand attacker techniques.
In partnership with Elysian Communication Private Limited, a leader in IT & network security solutions, this article outlines a comprehensive 10-step approach to Malware Investigation and how businesses can leverage professional services to strengthen their security posture.

In today’s digital era, enterprises face persistent cyber threats. Among these, malware remains one of the most insidious and damaging vectors. Whether it’s ransomware, trojans, worms or advanced persistent threats, the ability to conduct a thorough Malware Investigation is non-negotiable. The first step is recognizing that detection alone is insufficient you must investigate.
When you engage Elysian Communication Private Limited based in Madurai, Tamil Nadu, India – you gain access to a specialist team focused on IT infrastructure, network security, and digital threat management.
This blog post will walk you through:
- What a Malware Investigation is
- Why it’s critical for modern businesses
- A 10-step process you can follow (with the help of Elysian)
- How Elysian’s services integrate into that process
- Common FAQs about Malware Investigation
- A conclusion summarizing the key takeaways
1. What is Malware Investigation?
Malware Investigation is the structured process of examining malicious software to discover what it does, how it entered the system, what damage it may cause, and how to prevent future incidents. It often includes:
- Static code analysis
- Dynamic behaviour analysis
- Forensic review of impacted systems
- Intelligence collection on threat actors
The objective of Malware Investigation is not simply stopping the malware in its tracks—but understanding it deeply so that your organization can build resilient defences, refine incident response, and limit future exposure.
2. Why Malware Investigation Matters
Here are the key reasons why a robust Malware Investigation is vital:
- Threat landscape complexity: Malware strains evolve constantly, so a simple antivirus signature is no longer sufficient.
- Damage limitation: Early investigation means quicker containment, less data loss, and less business disruption.
- Legal, regulatory & reputational risks: Many industries require incident reporting; understanding the root cause through an investigation helps meet compliance and minimise reputational harm.
- Learning & strengthening defences: Investigation provides actionable insights, enabling organisations to improve controls, patch gaps, and train personnel.
- Proactive security posture: With a formal Malware Investigation capability, businesses shift from reactive to proactive security.
By partnering with Elysian Communication Private Limited, you can access a team experienced in security audits, vulnerability assessments and managed IT services that underpin effective Malware Investigation strategies.

3. 10 Essential Steps in a Malware Investigation
Conducting a Malware Investigation is a structured, strategic, and technically rigorous process. It involves more than just identifying a malicious program it’s about uncovering how it got in, what it did, and how to ensure it never happens again.
Below is a comprehensive step-by-step framework you can adopt with the expert guidance of Elysian Communication Private Limited — to perform an effective, results-driven Malware Investigation.
Step 1: Preparation & Planning
Preparation is the cornerstone of every successful Malware Investigation. Before any incident occurs, organizations must establish a clear investigation roadmap.
This involves:
- Defining scope and objectives — What systems, networks, and endpoints are critical to protect?
- Identifying threat models — Understanding potential attack vectors and adversary motivations.
- Establishing forensic readiness — Ensuring that data logging, backups, and monitoring are in place for quick access to evidence.
- Training the response team — Preparing cybersecurity personnel to respond quickly and methodically.
Elysian Communication Private Limited assists businesses in designing this foundational structure through risk assessments, security audits, and readiness programs. Their proactive planning ensures that every future Malware Investigation is organized, efficient, and legally defensible.
Step 2: Detection & Initial Triage
The detection phase is where your Malware Investigation begins. It starts when an anomaly is detected unusual network activity, unauthorized file modifications, or system performance drops.
During initial triage, the goal is to determine:
- Which systems or users are affected.
- The severity of the potential compromise.
- Whether the issue is truly malware-related or a false positive.
Elysian Communication Private Limited’s managed detection and response (MDR) solutions use advanced monitoring tools and real-time analytics to flag threats early.
Step 3: Isolation & Containment
Once malware is confirmed, isolation becomes the most critical action to prevent its spread.
This step ensures that infected systems are cordoned off from the main network to stop further contamination.
Elysian Communication Private Limited employs a containment-first approach, which includes:
- Network segmentation: Restricting communication between compromised and healthy devices.
- Access control enforcement: Temporarily suspending user accounts or system access.
- Endpoint quarantine: Using endpoint detection systems to isolate affected devices automatically.
Step 4: Evidence Collection & Preservation
Every credible Malware Investigation hinges on strong evidence. The integrity of digital artifacts directly determines the accuracy of the analysis.
Key actions in this phase include:
- Capturing disk images, system memory dumps, and network traffic logs.
- Securing event logs from operating systems, servers, and applications.
- Maintaining a forensic chain of custody, ensuring evidence authenticity.
Elysian Communication Private Limited emphasizes forensic precision using industry-standard methodologies to collect and safeguard digital data. Their approach ensures that your evidence remains admissible in internal audits, regulatory reviews, or even legal proceedings, if necessary.
Step 5: Static Analysis
Static analysis is the first deep-dive into the malware sample itself performed without executing the code.
This step helps analysts understand what the malware is capable of before they ever run it in a test environment.
During static analysis, the Malware Investigation team examines:
- File headers, imports/exports, and embedded resources.
- Binary code structure, strings, and metadata.
- Cryptographic signatures and suspicious code sections.
Elysian’s technical experts leverage sophisticated reverse-engineering tools to deconstruct malware safely. This non-invasive method helps determine the malware’s intent, communication patterns, and potential targets while maintaining a secure environment.
Step 6: Dynamic Behaviour Analysis
Static analysis provides insight into what the malware could do; dynamic analysis reveals what it actually does.
In this stage of the Malware Investigation, the malware sample is executed inside a controlled sandbox environment to observe its live behaviour.
Elysian’s secure lab environments allow analysts to track:
- File and registry modifications.
- Process creation and system-level calls.
- Network communications with command-and-control (C2) servers.
- Attempts at data encryption or exfiltration.
By monitoring these real-time interactions, Elysian Communication Private Limited builds a complete behavioural profile of the malware, enabling precise detection of its lifecycle and infection chain.
Step 7: Root Cause & Attack Path Analysis
Identifying malware behaviour is only part of the picture understanding how it got in is equally vital.
This step of the Malware Investigation focuses on uncovering the root cause and attack vector.
Elysian’s analysts trace the malware’s journey across systems by investigating:
- How the threat entered (phishing, drive-by downloads, infected USBs, etc.).
- Exploited vulnerabilities or misconfigurations.
- Privilege escalation and lateral movement techniques used by attackers.
Through in-depth network and endpoint analysis, Elysian pinpoints weaknesses in your security posture and provides actionable insights to close those gaps, ensuring similar attacks cannot recur.
Step 8: Impact Assessment
Understanding the scale of damage caused by malware is essential for informed decision-making. The Malware Investigation must quantify the impact both technically and financially.
Elysian Communication Private Limited conducts a comprehensive impact evaluation, including:
- Identifying data exfiltration or corruption.
- Measuring downtime and productivity loss.
- Assessing potential breaches of compliance or customer trust.
- Evaluating operational disruption and financial exposure.
This evidence-based assessment helps leadership teams gauge the true cost of compromise and prioritize remediation actions that yield maximum protection.
Step 9: Remediation & Recovery
Once the malware has been analyzed and its impact measured, it’s time to neutralize and restore.
The remediation stage focuses on eliminating the malware, repairing the damage, and reinstating secure operations.
Elysian’s experts guide this phase of the Malware Investigation through:
- Complete malware eradication using trusted removal tools.
- Patch management to address exploited vulnerabilities.
- System restoration from verified backups.
- Network hardening and updated access controls.
Their IT infrastructure management and disaster recovery solutions ensure your organization resumes operations quickly and securely, minimizing financial and reputational loss.
Step 10: Reporting & Lessons Learned
The final stage of the Malware Investigation process is also the most strategic documenting findings and transforming them into long-term improvements.
Elysian Communication Private Limited assists organizations in creating detailed post-incident reports that include:
- A timeline of events and technical findings.
- The root cause and propagation path of the malware.
- Assessment of impact and response effectiveness.
- Recommendations for improving policies, technologies, and training.
This stage also involves knowledge transfer and awareness sessions for employees, ensuring that your organization becomes stronger and more cyber-resilient after every incident. Elysian believes that every Malware Investigation should end with insight, not just resolution.
4. How Elysian Communication Private Limited Supports Your Malware Investigation
When you partner with Elysian Communication Private Limited, you gain access to a full-service IT & security provider based in Madurai, Tamil Nadu, with strong focus on digital infrastructure, network security, data protection, and proactive managed services.
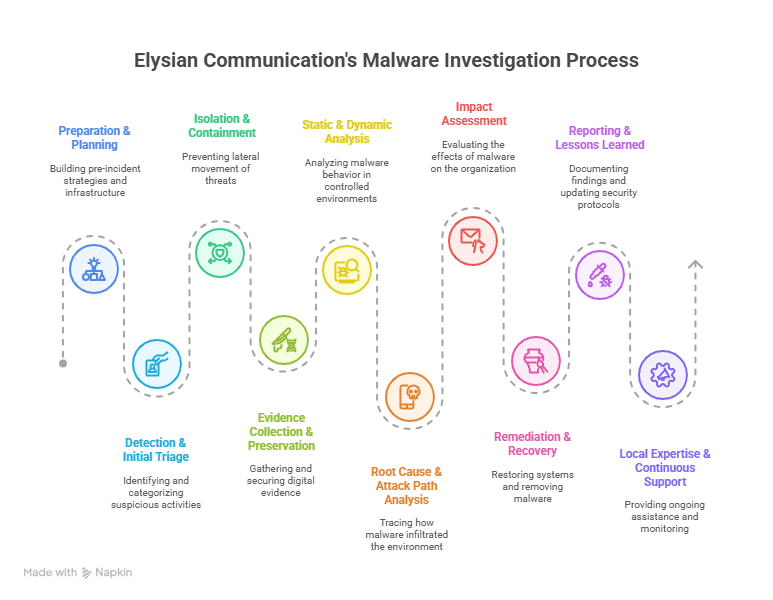
How Elysian Communication Private Limited Aligns with Each Stage of the Malware Investigation Framework
When a cybersecurity incident occurs, timing, expertise, and methodology determine the outcome. A well-structured Malware Investigation process requires not only technical skills but also a mature IT ecosystem and experienced guidance. This is where Elysian Communication Private Limited becomes your trusted partner.
With a proven track record in IT infrastructure, network security, and digital forensics, Elysian supports every stage of your Malware Investigation journey from preparation to post-incident review. Here’s an in-depth look at how Elysian services align with each investigative phase:
1. Preparation & Planning
The foundation of an effective Malware Investigation begins long before an incident happens. Elysian Communication Private Limited assists organizations in building robust pre-incident strategies through:
- Security Audits & Risk Assessments: They identify vulnerabilities across your network, endpoints, and applications to map your current risk landscape.
- Policy & Framework Design: Elysian helps define roles, responsibilities, and workflows for incident response and malware investigations, ensuring every team member knows what to do during a breach.
- Tool & Infrastructure Readiness: From sandboxing environments to endpoint monitoring tools, Elysian ensures your organization has the right technology stack for efficient malware analysis and digital forensics.
By laying this groundwork, your business becomes investigation-ready able to act decisively when malware strikes.
2. Detection & Initial Triage
When suspicious activity is detected, time is of the essence. Elysian’s Managed Security Services provide 24/7 monitoring through advanced alerting systems that flag potential threats at the earliest signs.
Their approach includes:
- Threat Intelligence Integration: Correlating global threat feeds with local network data to detect emerging malware patterns.
- Automated Alerts & Incident Escalation: Quick identification and categorization of suspicious files or processes enable faster triage.
- Human-Led Analysis: Elysian’s cybersecurity experts review automated alerts to validate incidents and determine if a full Malware Investigation is necessary.
This ensures rapid containment and prevents threats from escalating into larger breaches.
3. Isolation & Containment
Once a threat is confirmed, containment is critical to stop lateral movement within your network. Elysian Communication Private Limited employs multiple strategies to achieve this:
- Network Segmentation: Compromised systems are quickly isolated to prevent infection spread.
- Access Control Enforcement: They tighten user permissions and implement network-level blocks to minimize malware reach.
- Incident Playbooks: Predefined workflows guide the team to contain threats methodically and maintain forensic integrity.
By leveraging these techniques, Elysian ensures the Malware Investigation can proceed safely without further damage to business operations.
4. Evidence Collection & Preservation
A successful Malware Investigation depends on the accuracy and integrity of collected evidence. Elysian Communication Private Limited follows strict forensic principles:
- Data Capture: Collects system images, volatile memory dumps, logs, and network traffic samples without altering evidence.
- Chain of Custody Management: Every artifact is documented and stored securely, preserving evidential value for potential legal or regulatory proceedings.
- Forensic Tooling: Elysian uses advanced forensic platforms and ensures evidence integrity through cryptographic hashing and secure storage.
This meticulous process guarantees that the Malware Investigation findings are credible, reproducible, and compliant with cybersecurity standards.
5. Static & Dynamic Analysis
After evidence is secured, understanding the malware’s behavior becomes the next goal. Elysian Communication Private Limited provides the infrastructure and technical guidance to conduct:
- Static Analysis: Analysts examine malware binaries, code structures, and file metadata without executing the sample. This helps identify indicators of compromise (IOCs) and malicious intent.
- Dynamic Analysis: In a secure sandbox or isolated lab, the malware is executed under controlled conditions to observe its runtime behaviour network calls, file modifications, and registry alterations.
Elysian’s lab environments and analytical frameworks ensure safe, repeatable Malware Investigation workflows that reveal how malware operates and what it targets.
6. Root Cause & Attack Path Analysis
Once malware behavior is known, the next step is to trace how it infiltrated the environment. Elysian Communication Private Limited brings its network security and architectural expertise to uncover:
- Initial Attack Vectors: Whether malware entered via phishing emails, malicious websites, or compromised credentials.
- Privilege Escalation and Movement: Identifying how attackers gained deeper access to internal systems.
- System Vulnerabilities: Highlighting the misconfigurations or outdated software that facilitated the breach.
Through this stage of Malware Investigation, Elysian ensures that every technical weakness is mapped and addressed closing the loop between cause and consequence.
7. Impact Assessment
Understanding the real-world effects of malware is crucial for decision-making. Elysian helps organizations measure:
- Scope of Infection: Which systems and users were affected.
- Data Exposure: Whether sensitive or personal data was accessed or exfiltrated.
- Business Downtime & Financial Loss: Evaluating operational disruption and cost implications.
- Regulatory Exposure: Assessing potential compliance violations.
This structured assessment ensures that the Malware Investigation produces actionable intelligence, allowing leadership to quantify risk and communicate accurately with stakeholders.
8. Remediation & Recovery
Once the malware is analyzed and its effects understood, Elysian Communication Private Limited supports full remediation to restore normal operations:
- Malware Removal & Patch Management: Ensuring all traces of malicious code are eradicated and vulnerabilities patched.
- System Restoration: Recovering affected machines from clean backups while maintaining operational continuity.
- Infrastructure Repair: Addressing corrupted configurations, damaged databases, or disrupted services.
- Backup & Disaster Recovery Planning: Implementing proactive recovery strategies to protect against future incidents.
This phase marks the transition from reactive response to proactive resilience, making Elysian’s role in Malware Investigation both curative and preventive.
9. Reporting & Lessons Learned
A complete Malware Investigation doesn’t end with remediation—it ends with learning. Elysian ensures each incident becomes a catalyst for stronger security:
- Comprehensive Documentation: Detailed incident reports summarizing findings, root cause, impact, and corrective actions.
- Policy Updates: Revising security protocols, access controls, and patch management practices.
- Staff Awareness Programs: Conducting post-incident training sessions to strengthen organizational vigilance.
- Strategic Recommendations: Suggesting long-term improvements, including automation tools and monitoring enhancements.
This final step transforms a breach into an opportunity for growth, equipping organizations with knowledge that strengthens future defence.
10. Local Expertise & Continuous Support
Beyond methodology, Elysian’s greatest value lies in its ongoing partnership. Located in Madurai, Tamil Nadu, Elysian Communication Private Limited provides:
- On-Site Assistance: Rapid response and in-person support when digital incidents demand physical presence.
- Continuous Monitoring: 24×7 surveillance of systems to detect early signs of compromise.
- Consultative Approach: Tailored strategies based on your business size, sector, and regulatory requirements.
Engaging Elysian ensures your Malware Investigation process is not just a one-time event but part of a continuous cybersecurity lifecycle combining prevention, detection, and recovery into one cohesive service.
5. Frequently Asked Questions (FAQs)
Below are ten common questions about Malware Investigation with clear, concise answers:
1. What triggers a Malware Investigation?
A Malware Investigation is triggered when suspicious activity is detected such as unexplained system behaviour, alerts indicating malicious software, data exfiltration signs, or other anomalies.
2. How long does a full Malware Investigation take?
It depends on the scale and complexity of the incident some take hours, others days or weeks especially if systems, networks and multiple endpoints are involved.
3. Can I perform a Malware Investigation in-house or do I need to hire a specialist?
You can do basic investigations in-house if you have trained staff, tools and processes but for advanced threats it’s highly recommended to engage specialists (like Elysian Communication Private Limited) for expertise, infrastructure and legal/forensic compliance.
4. What tools are used in a Malware Investigation?
Typical tools include sandbox environments, reverse‐engineering software, memory and disk forensic tools, network packet captures, logging and SIEM systems, among others.
5. Does Malware Investigation guarantee no future breaches?
No process can guarantee zero future breaches. What a proper Malware Investigation does is reduce risk, strengthen defences, build awareness and improve readiness but maintaining security is an ongoing effort.
6. What should the report from a Malware Investigation include?
It should include: incident timeline, infected systems, malware behaviour and capabilities, root cause and entry point, business impact, remediation steps taken, lessons learned and recommendations for future.
7. Can Malware Investigation help with regulatory compliance?
Yes. Many regulations require investigations into data breaches or cybersecurity incidents. A documented Malware Investigation supports compliance, reporting and audit readiness.
8. How often should we conduct proactive Malware Investigations or assessments?
Regularly. While investigations usually follow incidents, proactive threat hunting, vulnerability assessments and mock investigations should be scheduled (e.g., annually or when major changes occur).
9. What is the difference between malware detection and Malware Investigation?
Detection is the action of identifying a potential threat. A full Malware Investigation goes further: analysing, contextualising, understanding, documenting and remediating the threat comprehensively.
10. Why choose Elysian Communication Private Limited for Malware Investigation support?
Because they combine IT infrastructure, network security, cloud, monitoring, audit and managed services providing a holistic environment in which to conduct effective Malware Investigation and remediate threats. Their expertise and regional presence (Madurai, Tamil Nadu) further enhance responsiveness.
6. Conclusion
In the ever-evolving threat landscape, your organisation cannot afford to simply detect threats it must understand them. A well-structured Malware Investigation equips you to do exactly that: uncover the what, how and why of malicious software incidents, measure their impact, and fortify your defences for the future.
By following the 10-step framework outlined above, and partnering with a professional service provider such as Elysian Communication Private Limited, you ensure that your investigation is not just technical but aligned to business continuity, regulatory needs and risk management.
Ready to elevate your cybersecurity posture? Contact Elysian Communication Private Limited, and make Malware Investigation a proactive part of your security strategy.





