The Ultimate Platform For
Seamless Data Center
Optimize your IT infrastructure with confidence. We provide expert strategies to assess, plan and transition
data centers with minimal downtime and maximum efficiency. Tailored solutions for enterprises aiming for
future-ready operations.

KEY HIGHLIGHTS
An All-in-One Service That Delivers Results
We simplify complex data center migrations and transitions with a methodical, precision-driven approach. Our process ensures seamless continuity, safeguarding data integrity and minimizing operational disruption. With deep technical expertise, we address dependencies, risks, and scalability from day one. Strategic planning supports long-term infrastructure goals and future-proofing. The result is a smooth, secure transition aligned with your business objectives.
SCAN, ANALYZE, SECURE
Our Core Services
We lead the way in securing digital infrastructures, ensuring operational continuity through advanced technologies and cybersecurity.

Comprehensive Infrastructure Audits
End-to-end evaluation of existing IT systems, performance bottlenecks.

Strategic Transition Planning
Custom roadmaps for smooth data center migrations with risk mitigation strategies.

Cloud & Hybrid Integration
Seamless integration with cloud environments for enhanced flexibility and scalability.

Security & Compliance Review
Ensure regulatory alignment and secure data handling throughout the transition.
SCAN, IDENTIFY, CLEANSE
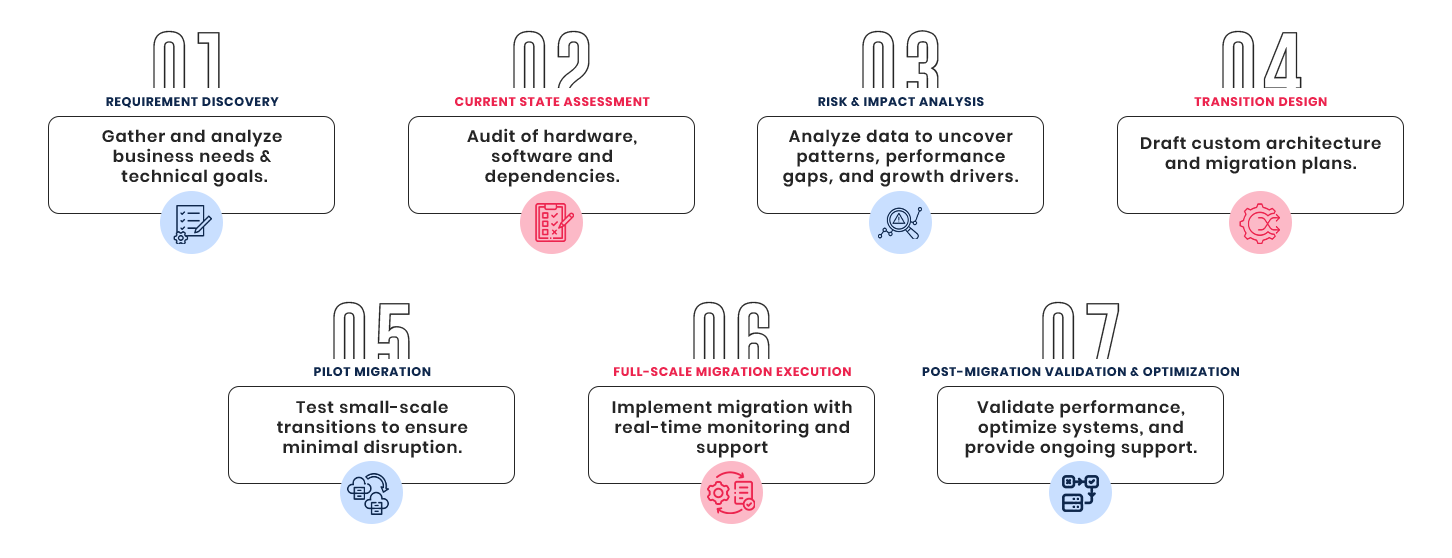
7 Stages Of Data Center Transition
We follow a structured and proven 7-stage workflow to ensure flawless execution:
WHY PARTNER WITH US?
Reliable, Scalable And Impact-Driven Solutions
With deep industry experience, our team delivers high-quality, cost-effective assessments tailored for modern enterprises. Whether you're consolidating, migrating, or modernizing, our approach guarantees success with minimized disruption.

Industry-Leading Expertise
Strategically-led assessments driven by certified professionals.

Proven Methodologies
Frameworks refined through real-world enterprise migrations.

End-to-End Support
From assessment to execution, we stay by your side every step of the way.
OUR PRINCIPLES AT WORK
Success Stories In Transition & Assessment

Data Center Optimization
We restructured outdated systems and moved to a high-availability cloud model—cutting costs.

Application Transitioning
Handled mission-critical app transitions with zero downtime—ensuring business continuity.

Cross-functional Collaboration
Our client saw success through a joint approach involving IT, compliance, and business leaders.
FAQ
Clear Answers To Your Cyber Security Concerns
Explore quick, expert-backed answers to common questions about our services, helping you make informed decisions and understand our approach better.
What is a Data Center & Transition Assessment?
It’s a structured process that evaluates your current IT setup and provides a plan for a seamless, secure, and efficient transition.
Who should use this service?
Any organization planning to migrate, consolidate, or modernize their IT infrastructure, including cloud adoption and data center shifts.
How long does a typical assessment take?
The duration varies depending on the scope but generally ranges from 2 to 6 weeks, including discovery, planning, and reporting.
Do you handle the actual transition as well?
Yes, we provide end-to-end support, from assessment and planning to execution and post-migration validation.
What makes your approach different?
We blend technical precision with strategic insight, ensuring risk-managed transitions aligned with your business objectives.
Will the assessment disrupt my operations?
No, the assessment process is designed to be non-intrusive. It analyzes your current infrastructure and plans for smooth transitions without impacting daily operations.





