Analyze And Neutralize
Malicious Code
Our malware investigation service analyzes suspicious activity, detects hidden malicious software
and determines its origin, behavior and impact. This service helps you respond swiftly & effectively
to potential infections or security incidents.
PROTECT, IMPROVE, MITIGATE
Uncover Hidden Threats And Strengthen Response Readiness
When anomalies strike, our malware investigation service steps in. We dissect suspicious code, trace attack origins and map out impact areas to help you contain and eliminate threats. This advisory driven approach ensures your teams are equipped for fast recovery and future prevention.
EXAMINE, SECURE, STRENGTHEN
Malware Investigation
Analyze suspicious system behavior to detect, isolate and eliminate malware threats. Our investigation traces the source, evaluates the impact and provides recovery guidance to ensure full restoration and future threat prevention.

Behavioral Analysis
Monitor system behavior to identify abnormal activities that indicate malware presence or execution.

Malware Classification
Categorize the detected malware (e.g., ransomware, spyware, trojans) and pinpoint its origin and characteristics.

Impact Assessment
Evaluate the extent of infection, affected systems and data exposure to contain the spread effectively.

Incident Reporting
Deliver detailed reports with mitigation steps, data recovery options and security reinforcement recommendations.
DETECT, DISRUPT, DEFEND.
Benefits Of Malware Investigation
Rapid and intelligent malware detection is critical to minimizing damage. Investigations provide clarity, containment and confidence in recovery.


STRENGTHEN, IDENTIFY, PROTECT
Find The Root. Defend The Future.
Analyze malicious activity, eliminate threats and reinforce your digital ecosystem.
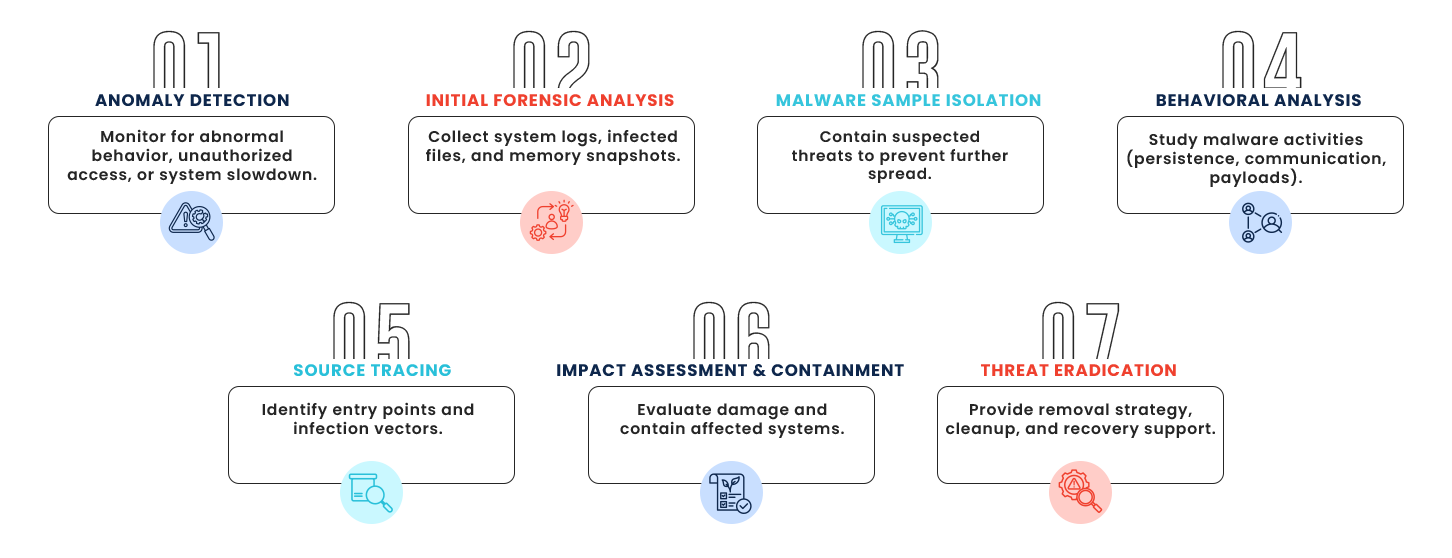
WHY CHOOSE US?
Malware Investigation
With expert driven strategies, cutting-edge tools and a client first mindset, we deliver tailored solutions that secure your digital assets with precision and reliability.

Real-Time Threat Isolation
Quickly identify and isolate malware to stop the spread before damage escalates

Forensic Level Insights
Understand the origin, behavior and full lifecycle of advanced threats.

Impact Analysis & Containment
Limit business disruption through fast, informed response planning.
OUR APPROACH
Our Core Principles

Government
We’ve assisted government departments in tracing sophisticated malware attacks. Our investigations helped uncover threat actors, neutralize infections and reinforce national digital infrastructure.

IT Enterprises
We supported IT firms in identifying root causes of repeated malware outbreaks. Our deep dive forensics led to faster recovery and improved endpoint protection strategies.

Logistics & Supply Chain
Malware in operational systems can halt services. We’ve helped logistics companies proactively isolate and eliminate threats, ensuring business continuity and minimizing downtime.
FAQ
Clear Answers To Your Cyber Security Concerns
Explore quick, expert-backed answers to common questions about our services, helping you make informed decisions and understand our approach better.
What types of malware do you investigate?
Ransomware, trojans, spyware, worms and more including custom malware.
Can malware investigations be done remotely?
Yes, we offer both remote and on-site investigation services.
How long does an investigation typically take?
It depends on complexity usually from a few hours to a few days.
Do you help with post-incident recovery?
Yes, including system cleanup, patching and response planning.




