In today’s rapidly digitalizing landscape, businesses of all sizes are turning to the cloud to gain agility, scalability, and cost-efficiency. However, this shift also heightens the need for robust cloud network security—an absolute necessity in safeguarding sensitive data, customer trust, and operational integrity. As cyber threats increase in complexity, securing your cloud environments is no longer optional but a foundational business requirement. At Elysian Communication, we specialize in delivering ironclad solutions tailored to each organization’s unique needs, ensuring your journey to the cloud is both secure and seamless.
What Is Cloud Network Security?
Cloud network security encompasses a comprehensive set of tools, strategies, and protocols aimed at protecting cloud-based systems from both internal vulnerabilities and external attacks. It involves securing data, applications, and infrastructure within cloud environments to ensure confidentiality, integrity, and availability. As businesses migrate workloads and sensitive information to public, private, or hybrid clouds, maintaining the confidentiality, integrity, and availability of data becomes paramount. Comprehensive covers every layer—networks, applications, data, and user access—ensuring protection against data breaches, ransomware attacks, misconfigurations, and insider threats. It acts as your digital shield and is essential for business continuity in an interconnected world.
Why Cloud Network Security Matters
With enterprises increasingly utilizing cloud services, malicious actors are adapting their strategies to exploit new vulnerabilities. High-profile breaches, compliance penalties, and reputational harm all underscore why investing in cloud network security is a strategic imperative. Regulatory environments are also evolving, as standards like HIPAA, GDPR, and ISO 27001 place the onus on organizations to protect client data in the cloud. Beyond risk mitigation, strong cloud network security enhances customer trust, strengthens brand reputation, and supports uninterrupted operations even during attempted attacks.
The Pillars of Cloud Network Security
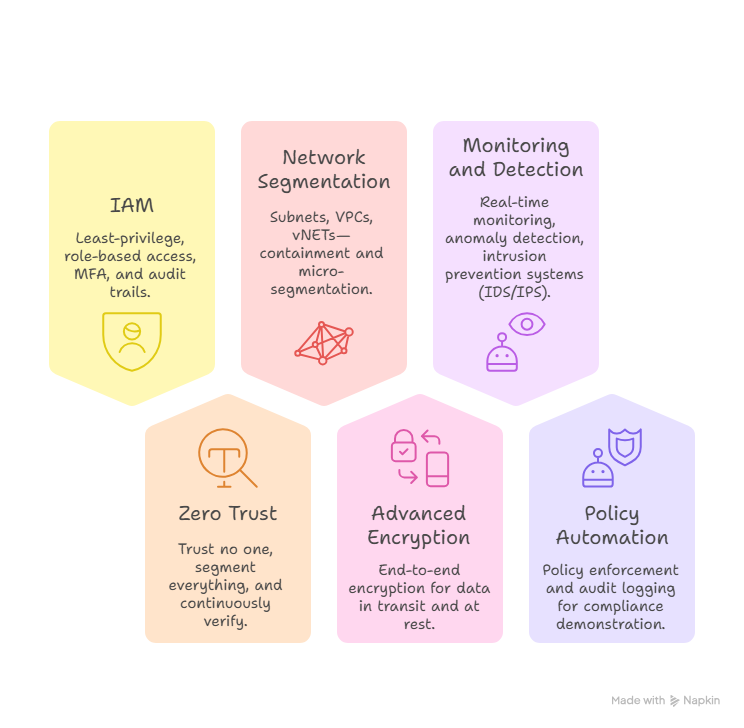
A robust approach to cloud network security stands on several key pillars:
- Identity and Access Management (IAM):
Controls and manages user access by enforcing the principle of least privilege, significantly reducing the risk of insider threats and unauthorized activity within the cloud environment. - Zero Trust Architecture:
Operates on a “never trust, always verify” model—segmenting and protecting every network component. - Network Segmentation and Isolation:
Segments cloud networks into isolated, secure zones to contain potential breaches and minimize the risk of lateral movement by attackers within the environment. - Advanced Encryption:
Protects data both in transit and at rest, making intercepted information useless to attackers. - Monitoring and Threat Detection:
Employs real-time analysis and machine learning to detect and block anomalous activities swiftly. - Policy and Compliance Automation:
Adopts tools that automate security controls and help prove regulatory compliance whenever needed.
Each pillar reinforces your overall activity, creating a layered defense that is resilient to evolving threats.
Components of Cloud Network Security
A fully realized cloud network security framework, like those implemented by Elysian Communication, integrates several components:
- Firewalls and Traffic Filtering:
Next-generation firewalls control and filter incoming/outgoing traffic, blocking unauthorized attempts. - Intrusion Detection and Prevention Systems (IDS/IPS):
Regularly monitor network traffic in real time to detect and eliminate potential threats or suspicious behavior before they can cause harm. - Access Control Systems:
Implement strong authentication protocols such as multi-factor authentication (MFA) and single sign-on (SSO) to enhance access security and prevent unauthorized entry. - Encryption Tools:
Automate encryption processes and manage cryptographic keys to secure sensitive data. - Endpoint Security:
Protects user devices and servers from being exploited as attack vectors. - Monitoring Tools:
Security Information and Event Management (SIEM), log analysis tools, and behavioral analytics ensure continual surveillance.
By combining these tools, cloud network security becomes proactive—not just responding to threats, but preventing them before any damage is done.
Cloud Network Security in Practice
To illustrate, let’s explore scenarios where cloud network security is both mission-critical and transformative:
- Multi-cloud & Hybrid Environment Security: Secure workloads that span AWS, Azure, and Google Cloud by harmonizing security controls and automating compliance checks.
- Case Study 1: A logistics provider enhanced by tightening AWS S3 access, automating permission reviews, and integrating proactive monitoring with Elysian Communication’s solutions.
- Case Study 2: During a healthcare cloud migration, multi-layer encryption and rigorous access controls helped achieve HIPAA and GDPR compliance without slowing operations.
- Case Study 3: A fintech startup integrated DevSecOps, adopting automated vulnerability scans, real-time policy enforcement, and cloud network security best practices across the CI/CD pipeline.
These examples demonstrate the practical steps businesses of any size can take to build truly secure cloud infrastructures.
The 7-Stage Cloud Network Security Lifecycle
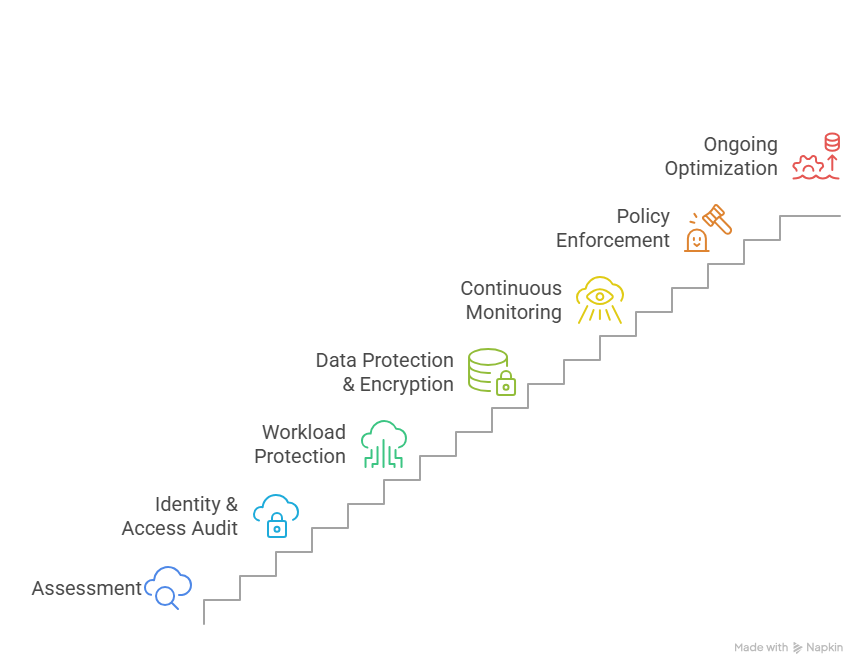
At Elysian Communication, we implement a seven-stage methodology for continuous cloud network security:
- Assessment: Evaluate your current cloud security posture, identifying gaps and areas for improvement.
- Identity & Access Audit: Hunt for privilege escalation risks and misconfigurations.
- Workload Protection: Harden virtual machines (VMs), containers, and microservices with best security practices.
- Data Protection & Encryption: Evaluate data sensitivity and apply encryption both at rest and in transit to safeguard against unauthorized access and ensure data integrity.
- Continuous Monitoring: Deploy real-time threat detection and alert systems to quickly identify and respond to suspicious activities across your cloud environment.
- Policy Enforcement: Leverage automated compliance and security policy enforcement tools.
- Ongoing Optimization: Evolve your security posture to adapt to new vulnerabilities and compliance requirements.
Each phase is essential for building and maintaining resilient cloud network security.
Cloud Network Security Best Practices Checklist
For any business looking to protect their cloud assets, here are tested cloud network security best practices:
- Leverage IAM and enforce least privilege access.
- Mandate MFA everywhere.
- Segment networks to minimize attack surfaces.
- Encrypt all sensitive information.
- Regularly update firewall and IDS rules.
- Perform ongoing vulnerability scans and penetration tests.
- Automate policy enforcement and compliance checks.
- Always audit cloud configurations and permissions.
- Provide ongoing security awareness training for all staff.
Deploying these practices ensures cloud network security remains robust even as technology and threats evolve.
Common Threats and Defense Strategies
Cloud environments face diverse threats:
- Phishing Attacks: Trick users into revealing credentials; tackled with security awareness and access controls.
- Credential Theft: Prevented with MFA and regular password changes.
- Misconfiguration: Eliminated through automated configuration management and regular audits.
- DDoS Attacks: Mitigated by scalable security policies and advanced firewalling.
- Insider Threats: Counteracted by detailed monitoring, strict IAM, and behavioral analytics.
Elysian Communication counters these challenges using automated cloud network security tools, real-time monitoring, and policy-driven defenses.
Compliance & Regulatory Considerations
Major regulations—including HIPAA, GDPR, SOC 2, and ISO 27001—demand stringent data protection in the cloud. Cloud network security ensures compliance by automating audit logs, encrypting critical data, and maintaining documentation for regulators. Businesses adhering to these frameworks not only avoid costly fines but also bolster stakeholder confidence.
Cloud Network Security for Organizations of All Sizes
A widespread misconception is that robust is only essential for large corporations, when in reality, businesses of all sizes are vulnerable to cyber threats. In reality, startups and small businesses face equal, if not greater, risks from cyber threats and data loss. With scalable solutions, cloud network security can be tailored to a company’s size, growth stage, and regulatory obligations. Elysian Communication’s flexible platforms allow organizations to pay only for the coverage they need, adapting as their infrastructure evolves.
Frequently Asked Questions
1. What are the core components of an effective cloud network security strategy?
This question helps readers understand the building blocks of a secure cloud environment, including firewalls, IAM, encryption, and monitoring tools.
2. How does cloud network security differ from traditional on-premise security?
Clarifies the unique challenges and solutions in cloud environments compared to legacy infrastructure, educating readers on why cloud-specific strategies are essential.
3. What are the most common threats to cloud network environments today?
Addresses current risks like phishing, misconfigurations, DDoS attacks, and insider threats, providing context for why layered security is necessary.
4. How can businesses ensure compliance with regulations like HIPAA or GDPR in the cloud?
Helps businesses understand the compliance landscape and how cloud network security supports audit readiness, encryption, and data privacy mandates.
5. Why is continuous monitoring crucial for cloud network security?
Explains the importance of real-time threat detection and proactive responses, especially as threats evolve rapidly in cloud infrastructures.
Integrating Cloud Network Security Into Your Workflow
Modern organizations thrive when security is embedded into every stage of their workflow. By integrating cloud network security into DevOps and CI/CD pipelines, businesses ensure new applications and updates are secure from the outset. Automation reduces manual overhead, increases development velocity, and fortifies the company against breaches. With security as a built-in element, rather than a bolt-on, organizations gain peace of mind and regulatory assurance.
Why Choose Elysian Communication
When selecting a cloud network security partner, expertise and comprehensive support matter most. Here’s why Elysian Communication is the trusted choice for businesses across sectors:
- Deep Multi-Cloud Expertise: Our engineers secure AWS, Azure, GCP, and hybrid deployments with unified strategies.
- End-to-End Coverage: From strategic planning to 24/7 threat monitoring, we cover every aspect of cloud network security.
- Regulatory Mastery: We have proven experience guiding companies through HIPAA, GDPR, ISO 27001, and more.
- Automation & DevSecOps: We streamline security to maximize agility and minimize complexity.
- Continuous Innovation: Our solutions adapt constantly to the latest threats and regulatory updates.
- Customer First: Every engagement is tailored and transparent, prioritizing your business goals.
Partnering with Elysian Communication means you never face cyber risks alone—your data, workloads, and reputation are always in safe hands.
Action Plan—Getting Started With Cloud Network Security Today
Ready to strengthen your cloud security approach and stay one step ahead of emerging cyber threats?
Here’s a step-by-step action plan to elevate your organization’s cloud network security:
- Audit Your Current Security Posture: Identify gaps and vulnerabilities across your cloud infrastructure.
- Prioritize Critical Workloads: Determine which data and systems need the highest level of protection.
- Consult With a Provider: Elysian Communication offers personalized assessments and solution roadmaps.
- Implement Advanced Security Tools: Deploy firewalls, monitoring, and encryption across all environments.
- Train Your Teams: Empower employees to recognize threats and adhere to security best practices.
- Conduct Regular Reviews and Optimization: Establish routine security assessments to stay ahead of emerging threats and ensure ongoing compliance with industry standards and regulations.
By following these steps, you create a proactive, layered, and future-proof approach to cloud network security.
Conclusion
In the digital era, cloud network security is the cornerstone of business resilience, customer trust, and regulatory compliance. With sophisticated threats targeting cloud environments, organizations need more than basic protections—they need strategically layered, intelligent defenses that evolve with the threat landscape. Elysian Communication leads the way by delivering tailored, robust, and scalable cloud network security solutions to organizations across every industry. Now is the time to prioritize your security posture—consult with Elysian Communication and fortify your journey to the cloud, ensuring your assets, data, and reputation remain secure.
Your data deserves more than basic protection—fortify your cloud with layered, intelligent security.





