IoT Threat Simulation For
Smarter, Safer Systems
Our IoT Threat Simulation service mimics real-world attack scenarios on your IoT ecosystem to identify
vulnerabilities before attackers do. Smart sensors to connected industrial systems, we ensure a every
device and data flow is secure, resilient and fully test-ready.

KEY HIGHLIGHTS
Anticipate Threats. Validate Defenses.
We perform advanced attack simulations on your IoT infrastructure to uncover vulnerabilities in firmware, APIs, communication channels and edge devices. Our proactive approach mimics real-world cyber threats to identify and close security gaps before they can be exploited. We assess your IoT ecosystem’s resilience to breaches, tampering and unauthorized access. By testing against the latest attack vectors, we ensure your devices and data remain protected. Prepare your systems for real-world challenges with through and realistic threat simulations.
SCAN, ANALYZE, SECURE
Our Core Services
Simulate real-world attacks on IoT ecosystems to assess device and network exposure. Uncover vulnerabilities, misconfigurations and potential exploitation paths in connected environments.
EXAMINE. SECURE. STRENGTHEN
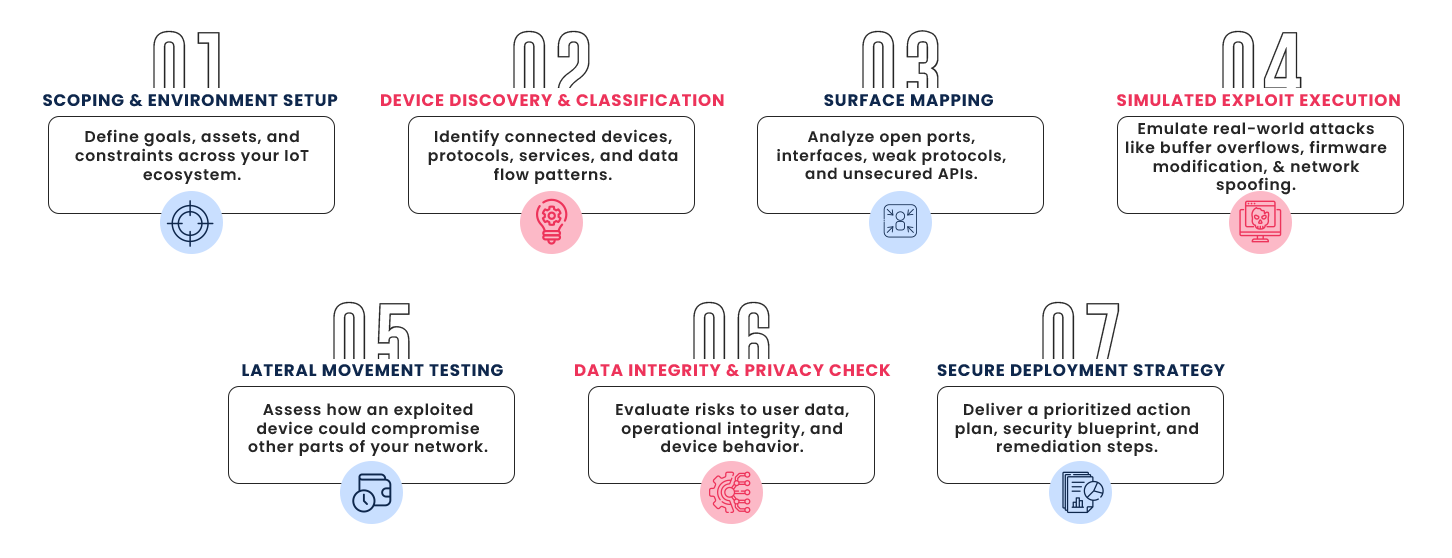
7 Stages Of IoT Threat Simulation
Our simulation process follows a meticulous 7 stage model designed for depth and accuracy:
WHY PARTNER WITH US?
Because Every Connected Device Is A Potential Attack Surface
Our simulations help secure your IoT infrastructure before attackers get a chance. With deep knowledge of IoT firmware, hardware interfaces and communication layers, we provide a level of insight that most generic pen tests miss.

Device Agnostic Testing
From consumer grade wearables to industrial control systems we test it all.

Real-World Attack Models
Our scenarios are modeled on tactics used by real threat actors, not just lab scripts.

Built for Scalability & Compliance
Secure new device rollouts while aligning with ISO/IEC 30141 and other IoT security frameworks.
OUR PRINCIPLES AT WORK
How We Help Organizations Lock Down IoT Risks

Industrial IoT Audit | Smart Factory Simulation
Simulated DDoS and firmware hijack on smart PLCs to uncover hidden firmware flaws and insecure bootloaders.

Smart Home Product Review | Startup Device Hardening
Tested API and mobile app interactions of a new consumer IoT product blocked data leakage paths pre-launch.

Healthcare IoT Security | Medical Device Threat Modeling
Performed threat simulations on hospital grade wearable devices to comply with HIPAA and FDA cybersecurity guidelines.
FAQ
Clear Answers To Your Cyber Security Concerns
Explore quick, expert-backed answers to common questions about our services, helping you make informed decisions and understand our approach better.
What is IoT Threat Simulation?
It’s a security testing process that simulates cyberattacks on IoT devices and infrastructure to expose vulnerabilities before they can be exploited.
Which devices can you test?
We test all types of IoT devices industrial, consumer, automotive, healthcare and more across protocols and firmware levels.
Is your testing destructive?
No. All simulations are conducted in controlled environments or sandboxes designed to avoid device damage or service disruption.
What kind of threats do you simulate?
We simulate real-world tactics including firmware attacks, MITM attacks, credential harvesting and network pivoting via IoT endpoints.
Will you help secure the findings?
Absolutely. Along with detailed reports, we provide patching guidance and long term hardening strategies for each threat discovered.
Why is IoT Threat Simulation important?
As IoT devices become more integrated into daily operations, their vulnerabilities present significant risks. Simulation helps identify and address security weaknesses before attackers can exploit them.









