Top-Tier IT & Network Audit
Tailored Solutions
We specialize in designing & deploying intelligent IT auditing strategies for global enterprises.
Our approach ensures compliance, mitigates risks, and strengthens your tech infrastructure.
Partner with us to turn audits into strategic business advantages.

EVALUATE. DETECT. SECURE
IT Auditing
Our IT auditing services help organizations assess infrastructure, ensure regulatory compliance, identify vulnerabilities, and enhance IT governance.
Audit & Assurance
We perform comprehensive IT audits ensuring your systems align with regulatory standards and internal policies, minimizing risks.
Risk Management
Our team identifies potential vulnerabilities and implements strategies to manage and mitigate risks across your IT ecosystem.
ANALYZE. IDENTIFY. FIX
Key Service Areas In IT Auditing
EXPOSE. EVALUATE. FORTIFY
Our Benefits
Gain a clear understanding of your current IT infrastructure, uncover security vulnerabilities, and ensure regulatory compliance. Our audits help optimize performance, reduce operational risks, and align your technology with business goals. With detailed assessments and expert recommendations, you’re empowered to make smarter IT decisions. Stay protected, efficient, and future-ready with our strategic IT auditing consultation.
Strategic Decision Support
Gain actionable insights that guide your IT investments and resource planning.
Improved Security Posture
Detect threats early and implement corrective actions before they escalate.
Improved Efficiency
Identify inefficiencies, reduce redundancies, and streamline IT operations.
Regulatory Confidence
Ensure readiness for audits and demonstrate compliance to stakeholders.
SCAN. ANALYZE. SECURE
7-Stage IT Auditing Process Flow
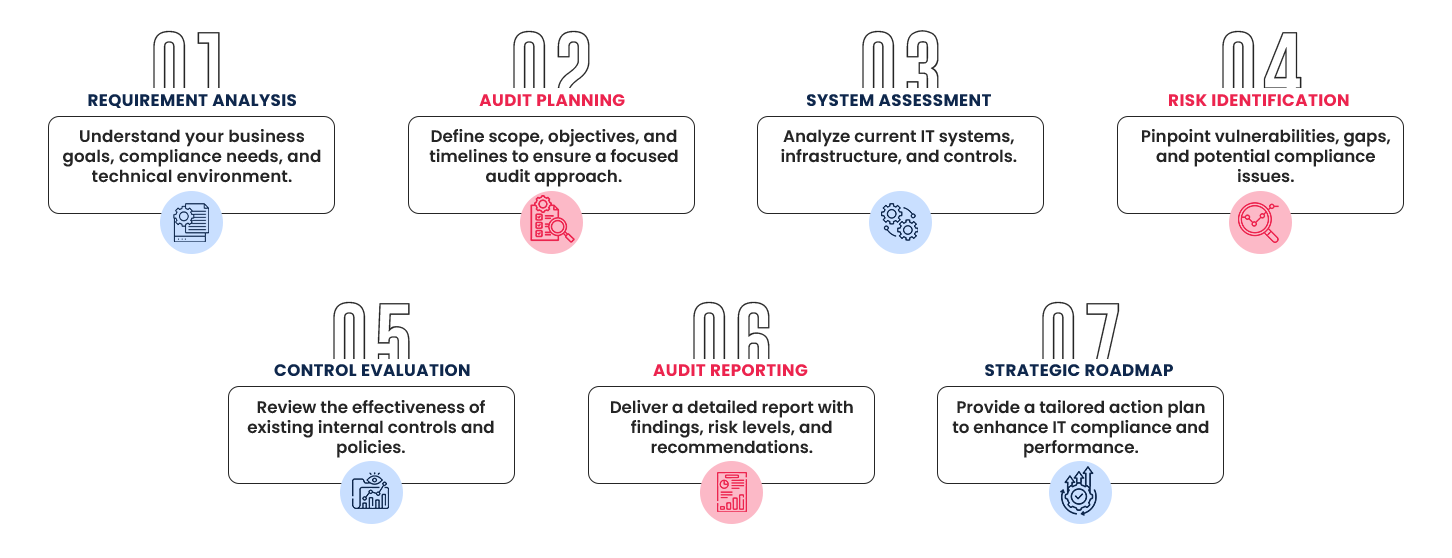
ANALYZE. IDENTIFY. FIX
Why Choose Us For IT Auditings
Trusted Financial & IT Expertise
Benefit from experienced consultants who bring deep knowledge across both IT and financial domains. We offer insights that bridge technology and business, ensuring holistic audit outcomes.
Tailored Consulting Solutions
Our audit strategies are designed around your specific operations, risk areas, and compliance needs. You receive personalized guidance that aligns with your goals and industry standards.
Comprehensive Legal & Compliance Support
Stay ahead of ever-changing regulations with dedicated legal and compliance advisory. We help you meet all industry standards while reducing regulatory risks and penalties.
Consulting
Our skilled consultants deliver strategic IT and financial insights to improve operational integrity. From planning to implementation, we support your business with clear, results-driven direction.
EXPOSE. EVALUATE. FORTIFY
Portfolio Highlights

Cloud Infrastructure Audit
Conducted a thorough audit of cloud architecture to ensure robust data protection and regulatory compliance. Enabled a multi-national SaaS provider to maintain secure, scalable.

Healthcare IT Compliance Review
Reviewed and optimized healthcare IT systems to meet HIPAA and GDPR compliance requirements. Enhanced patient data security while supporting seamless healthcare operations and reporting.

Retail Network Vulnerability Audit
Performed in-depth vulnerability assessment across a nationwide retail chain’s network. Mitigated security risks and strengthened defenses to protect customer and transaction data.
FAQ
Clear Answers To Your Cyber Security Concerns
Explore quick, expert-backed answers to common questions about our services, helping you make informed decisions and understand our approach better.
What is an IT audit?
An IT audit evaluates your organization’s IT systems, controls, and processes for security and compliance.
How often should we perform an IT audit?
Regular audits—typically annual or bi-annual—help ensure compliance and detect issues early.
What industries need IT auditing?
All industries benefit, especially finance, healthcare, education, and e-commerce.
What standards do you audit against?
We audit against global standards like ISO 27001, NIST, HIPAA, GDPR, and more.
Do you provide post-audit support?
Yes, we offer ongoing consultation, implementation guidance, and compliance planning.
What does an IT auditing consultation include?
An IT auditing consultation includes a comprehensive review of your IT systems, security protocols, data management practices, and compliance status to identify risks, improve efficiency, and provide actionable recommendations for enhancement.



