Uncover Hidden Vulnerabilities
Before Attackers Do
Threat exposure analysis identifies potential weaknesses in your IT environment by evaluating assets, attack
surfaces, and external/internal threats. Our proactive approach provides a comprehensive understanding of
risk factors, allowing you to take preemptive action and stay ahead of evolving cyber threats.
EXPOSE, REPAIR, PROTECT
Illuminate Hidden Risks And
Strengthen Your Security Posture
Gain a clear view of your organization’s threat landscape with our advanced threat exposure analysis. We help businesses uncover hidden vulnerabilities, assess critical risks, and develop proactive strategies to neutralize potential attacks. Through continuous monitoring and tailored insights, we empower you to stay steps ahead of cyber threats.
SCAN, ANALYZE, SECURE
Our Services
Identify hidden security gaps across your digital infrastructure. Our experts assess your threat landscape, highlight vulnerabilities, and provide actionable insights to reduce potential attack surfaces and strengthen your overall cyber posture.

Asset and Attack Surface Mapping
Pinpoint critical systems, applications, and entry points that could be targeted by attackers.

Vulnerability Prioritization
Categorize risks based on severity, exploitability, and business impact for focused remediation.

Threat Intelligence Integration
Leverage real-time threat data to assess exposure to current and emerging attack trends.

Strategic Risk Recommendations
Receive actionable guidance tailored to reduce attack vectors and improve posture.
SEE THE UNSEEN. SECURE THE UNKNOWN
Benefits Of Threat Exposure Analysis
Understanding your organization's vulnerability landscape is essential to building a strong security foundation. Threat Exposure Analysis enables businesses to proactively detect weaknesses, close security gaps, and build resilient digital ecosystems.


ANALYZE, IDENTIFY, FIX
Expose The Risk. Empower The Response.
Uncover hidden vulnerabilities across your digital landscape to proactively reinforce your defenses.
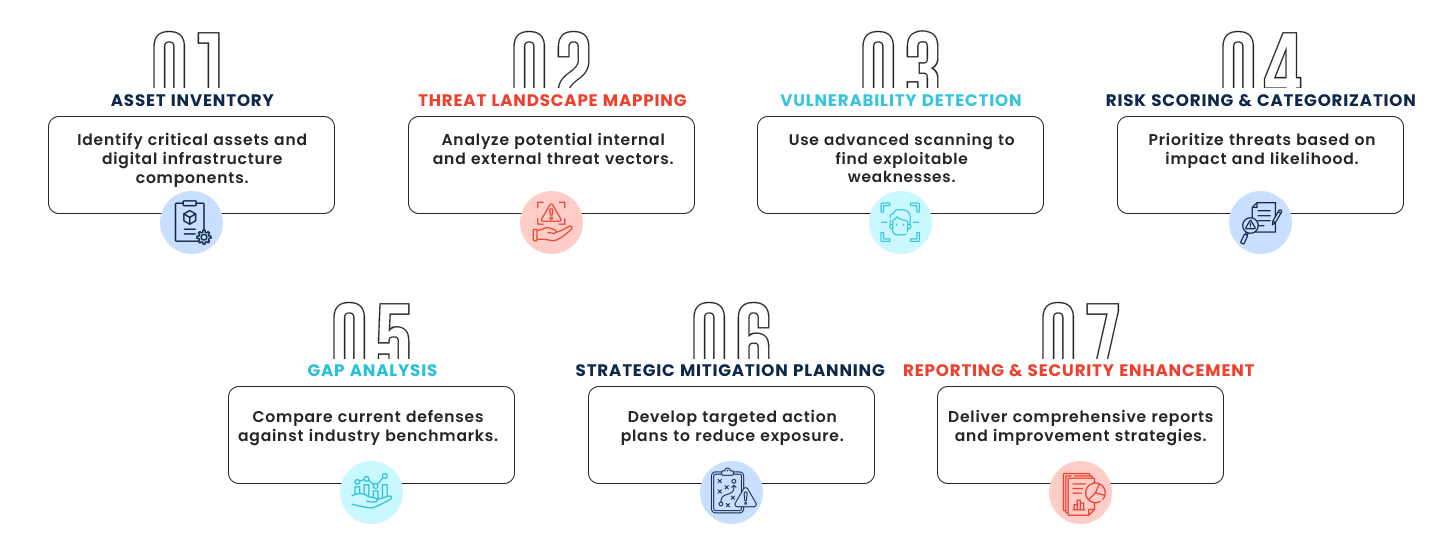
WHY CHOOSE US?
Your Trusted Business Partner
With expert-driven strategies, cutting-edge tools, and a client-first mindset, we deliver tailored solutions that secure your digital assets with precision and reliability.

End-to-End Threat Visibility
Gain full-spectrum visibility into hidden risks across your entire infrastructure.

Actionable Risk Intelligence
Receive prioritized, context-aware insights to make informed security decisions.

Custom Exposure Mapping
Our analysis adapts to your organization’s architecture and threat profile.
OUR APPROACH
Our Core Principles

Healthcare
We’ve worked with healthcare providers to uncover hidden vulnerabilities in critical systems. Our analysis helped secure patient data, ensured compliance, and strengthened trust through enhanced digital safety.

Banking
For financial institutions, we’ve mapped complex threat landscapes to highlight high-risk points. Our solutions enabled real-time monitoring and proactive mitigation, protecting assets and customer data.

Retail
We helped retail businesses assess third-party risks and secure transactional platforms. Our insights allowed clients to minimize data breaches and enhance customer confidence in e-commerce environments.
FAQ
Clear Answers To Your Cyber Security Concerns
Explore quick, expert-backed answers to common questions about our services, helping you make informed decisions and understand our approach better.
What is Threat Exposure Analysis?
It’s a method to identify, analyze, and assess potential security risks across your entire IT environment.
How often should I conduct a threat assessment?
Ideally, it should be conducted quarterly or after significant infrastructure changes.
Can it help prevent ransomware attacks?
Yes, it identifies exploitable vectors that ransomware can target and closes those gaps.
Is this different from a vulnerability scan?
Yes, it provides context-aware risk analysis rather than just listing open vulnerabilities.




