Powerful Wireless Intrusion
Testing To Safeguard Data
Secure your airspace with confidence. Our Wireless Intrusion Testing service uncovers vulnerabilities in your Wi-Fi
networks, helping you proactively prevent unauthorized access, rogue devices, targeted attacks & eavesdropping
before threats take hold.

KEY HIGHLIGHTS
Comprehensive Wi-Fi Security, Delivered Smartly
We perform in-depth testing that mimics real-world cyberattacks on your wireless infrastructure, going far beyond basic scans. Our assessment uncovers weak encryption methods, flawed configurations, and risky authentication setups. We detect insecure protocols and unauthorized access points that could be exploited by attackers. By identifying and addressing these vulnerabilities, we help fortify your wireless network from end to end. The result is a secure, resilient wireless environment ready to withstand modern threats.
EXAMINE. SECURE. STRENGTHEN
Our Core Services
Identify vulnerabilities in your wireless networks through controlled penetration testing. Protect against unauthorized access, rogue devices, and Wi-Fi-based threats.
STRENGTHEN. IDENTIFY. PROTECT
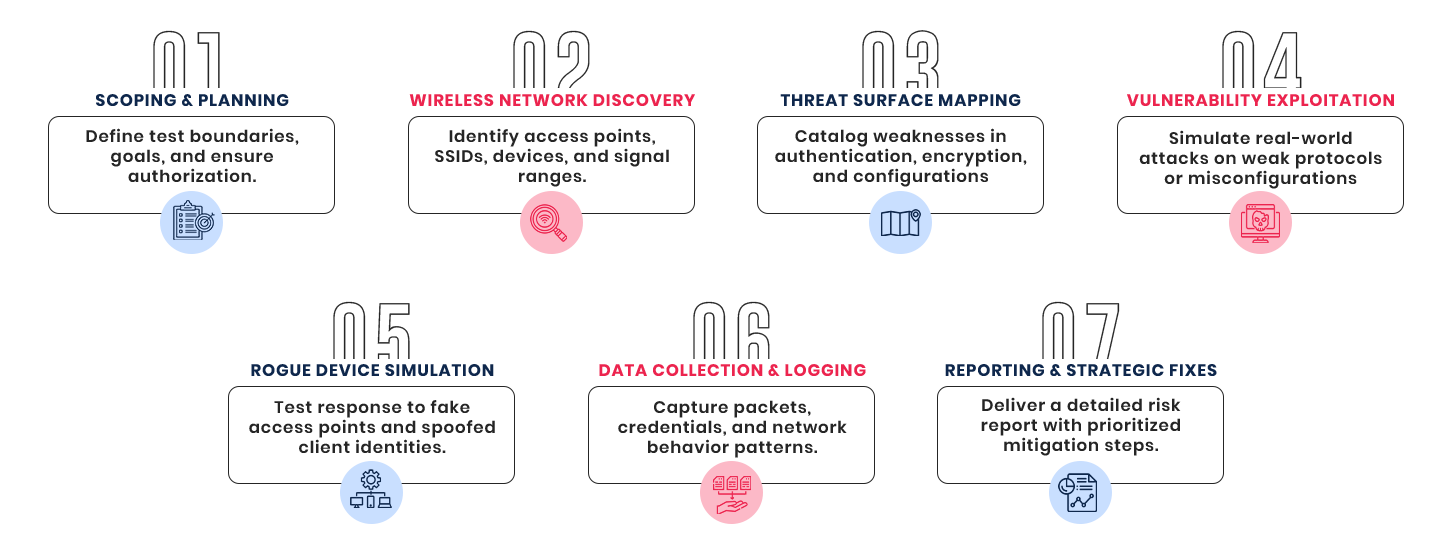
7 Stages Of Wireless Intrusion Testing
We follow a rigorous 7-stage methodology for effective testing and risk mitigation:
WHY PARTNER WITH US?
Next-Level Protection For A Wireless World
Our Wireless Intrusion Testing service is backed by certified ethical hackers and advanced testing tools. We offer the perfect blend of accuracy, discretion, and impact to help you build a secure wireless infrastructure.

Advanced Testing Tools
We leverage industry-leading suites like Aircrack-ng, Kismet, and Wireshark.

Tailored Test Scenarios
Simulations are customized to match your business environment and threat model.

Zero Disruption Guarantee
All testing is conducted with minimal to no impact on live systems.
OUR PRINCIPLES AT WORK
Client Success Through Strategic Wireless Testing

Secure Retail Chain Deployment
Identified and secured exposed guest networks and rogue APs across 30+ locations.

Executive Office Security
Tested and hardened high-value wireless segments to prevent executive data leaks.

Empowered IT Teams
Enabled internal teams with the tools and knowledge to manage wireless security post-assessment.
FAQ
Clear Answers To Your Cyber Security Concerns
Explore quick, expert-backed answers to common questions about our services, helping you make informed decisions and understand our approach better.
What is Wireless Intrusion Testing?
It’s a specialized penetration test that evaluates the security of your wireless networks, simulating potential attack scenarios.
Is this test safe for live networks?
Yes, all actions are non-destructive and carefully coordinated to ensure there’s no disruption to your systems.
What threats can it detect?
Weak encryption (WEP/WPA), rogue APs, signal leaks, MITM vulnerabilities, misconfigurations, and more.
How often should this test be conducted?
At least annually or after significant changes to your wireless setup, especially in high-risk environments.
Can you help fix the vulnerabilities you find?
Absolutely. We offer comprehensive remediation guidance and can work with your internal team to resolve issues.
What does the testing process include?
The process typically includes scanning for weak spots in your wireless network, testing for rogue devices, assessing encryption strength, and simulating attack scenarios to assess overall security.








