In today’s fast-evolving digital landscape, businesses are more vulnerable than ever to cyber threats. With sensitive data, customer information, and critical operations increasingly reliant on digital infrastructure, securing your network is no longer optional—it’s essential. That’s where a comprehensive network security audit comes into play. This guide explores the most effective tips for network security audit, helping organizations of all sizes identify vulnerabilities, protect their assets, and ensure regulatory compliance.
Network Security Audit
A network security audit involves a thorough assessment of an organization’s IT environment to uncover security weaknesses, evaluate current protective measures, and verify adherence to relevant industry regulations and standards. It involves analyzing hardware, software, policies, and user activities that impact the security of the entire network.
Network security audits generally fall into two categories: internal audits, which are performed by an organization’s own IT or security staff, and external audits, which are handled by independent cybersecurity professionals from outside the company. Both types play a vital role in applying practical tips for network security audit to detect issues early—before they escalate into costly breaches.
Regular audits help:
- Detect and resolve security gaps
- Prevent data loss and unauthorized access
- Ensure compliance with standards like ISO/IEC 27001, GDPR, HIPAA
- Build customer trust by demonstrating a commitment to security
Incorporating tips for network security audit early and often can save organizations from financial losses and reputational damage.
Why Network Security Audits Are Crucial in 2025
With remote work, cloud computing, and IoT becoming the new norm, cyber attackers have more entry points than ever before. In 2025, businesses must prioritize security by implementing effective tips for network security audit, not only for protection but also for operational efficiency.
Some key reasons for conducting regular network security audits include:
- Increased Threat Vectors: Cybercriminals now use AI and automation to exploit vulnerabilities faster.
- Regulatory Pressure: Data protection laws are stricter than ever.
- Financial Impact: Breaches cost businesses millions in recovery, fines, and lost revenue.
- Trust and Reputation: Customers prefer brands that safeguard their data.
Implementing proven tips for network security audit allows companies to identify weaknesses proactively, rather than reactively responding to threats.
Pre-Audit Preparation: Setting the Groundwork
Before you initiate an audit, it’s vital to lay a solid foundation. Proper preparation helps streamline the process and ensures that all critical areas are covered.
Steps for pre-audit readiness include:
- Define Scope & Objectives: Clearly outline what will be audited—systems, endpoints, user accounts, cloud infrastructure.
- List Critical Assets: Inventory all devices, databases, servers, and applications.
- Notify Stakeholders: Involve IT teams, department heads, and upper management.
- Assemble Documentation: Collect security policies, past audit reports, and incident logs.
Checklist Before Starting:
- Active directory logs
- Firewall and router configurations
- Patch history
- Antivirus status
- Network topology maps
Understanding these basics lays the foundation for applying in-depth tips for network security audit in the next phases.
Tips for Network Security Audit Execution
The actual execution of a network security audit involves a strategic blend of automated tools, manual inspection, and user behavior analysis. This stage is critical, as it provides actionable insights into the current state of your IT infrastructure. Below are essential and proven tips for network security audit execution that ensure no aspect of your network remains unchecked:
1. Run Vulnerability Scans
Use reputable tools like Nessus, OpenVAS, or Qualys to scan your network for known vulnerabilities. These tools compare your system against vast databases of known threats and misconfigurations. Regular vulnerability scanning helps you identify outdated software, unpatched systems, open ports, and risky protocols before attackers can exploit them.
2. Inspect Firewall Rules
Firewalls serve as the initial barrier protecting a network from unauthorized external access and cyber threats. Audit firewall configurations to ensure only essential ports, IP addresses, and services are allowed. Remove any outdated or unnecessary rules to reduce potential entry points. Log and monitor all traffic to detect abnormal patterns.
3. Check Access Controls
Review user permissions and group access rights thoroughly. Make sure each user has access only to the resources necessary for their job role—a principle known as least privilege. Disable unused accounts and routinely audit privileged accounts, which can be high-risk if compromised.
4. Review Patch Management
Security patches close vulnerabilities in operating systems, applications, and firmware. Verify that all systems, including third-party software and plugins, are fully updated. Implement a centralized patch management system to automate and monitor updates across all endpoints.
5. Monitor Antivirus Logs
Review antivirus and anti-malware solutions to ensure they are actively monitoring all endpoints. Inspect quarantine logs, threat history, and update schedules. Confirm that definitions are current and that scans are running regularly without interruption.
6. Examine Endpoints
Endpoints such as laptops, smartphones, printers, and IoT devices often fall outside the perimeter of routine audits. Each device connected to your network can be a potential backdoor for intrusions if not managed properly. Use endpoint detection and response (EDR) tools to monitor and secure these devices.
7. Assess Disaster Recovery Plans
Check whether your organization has a clearly defined and tested disaster recovery plan (DRP). Ensure data backups are recent, secure, and easily restorable. Simulate a data recovery exercise to test how quickly your system can bounce back from an attack or failure.
8. Check Remote Access Protocols
As remote work continues to rise, assessing all remote access mechanisms becomes a critical part of applying tips for network security audit. Ensure that Virtual Private Networks (VPNs) and remote desktop solutions are secured with robust encryption protocols and enforced multi-factor authentication (MFA). It’s equally important to log every remote session and regularly monitor for irregular access patterns, such as logins at unusual hours or from unexpected geographic locations. These measures help safeguard against unauthorized intrusions and data breaches.
Best Practices During the Audit
These strategies are key tips for network security audit that ensure a thorough and successful assessment process:
- Leverage Automated Tools for Efficiency: Tools like SIEM (Security Information and Event Management) platforms can help collect and analyze security data in real-time, highlighting anomalies quickly.
- Maintain Detailed Logs of All Findings and Actions: Keep a comprehensive record of every issue discovered, how it was addressed, and by whom. This ensures accountability and simplifies future audits.
- Prioritize Vulnerabilities Based on Risk Levels: Not all vulnerabilities are equal. Use a risk-based approach to focus remediation efforts on high-impact, high-likelihood issues first.
- Ensure Regulatory Compliance: Stay updated with evolving cybersecurity regulations and ensure that all audit activities align with industry standards like ISO 27001, NIST, PCI-DSS, or GDPR.
Common Mistakes to Avoid During a Network Security Audit
Even the most well-structured plans can fall short if common mistakes are overlooked. As part of essential tips for network security audit, be sure to watch out for these critical errors:
- Neglecting Internal Threats: Insider threats account for over 30% of breaches.
- Overlooking Device-Level Security: Personal laptops, smartphones, and tablets often lack proper protection, making them easy targets for cyber threats..
- Ignoring Unauthorized Tools: Applications and services installed without IT approval can operate unnoticed on the network, creating hidden security risks.
- Failing to Document: An undocumented issue is a future risk.
Proactive vs. Reactive Auditing
Proactive audits leverage predictive analytics and advanced monitoring to uncover potential vulnerabilities before they can be exploited, enabling organizations to stay ahead of threats. In contrast, reactive audits are conducted in response to a security incident. Adopting a forward-thinking approach and applying tips for network security audit proactively leads to stronger defenses, reduced risk exposure, and more resilient IT infrastructure.
Post-Audit Actions: What Comes Next
Once the network security audit is complete, the post-audit phase becomes crucial in turning observations into actionable strategies. This phase is where the real value of the audit is realized, and it’s essential not to overlook its significance.
Analyze Results: Categorize Findings by Severity
Start by thoroughly reviewing the audit report. Classify each finding based on its risk level—critical, high, medium, or low. This helps prioritize remediation efforts and ensures that the most serious threats are addressed first. Applying key tips for network security audit, look for patterns that may indicate systemic vulnerabilities.
Build a Remediation Plan
Once the findings are categorized, create a structured plan that assigns specific issues to responsible teams or individuals. Define clear timelines and expected outcomes. An effective remediation plan should also include communication protocols and escalation steps in case challenges arise.
Policy Revisions
Leverage the findings from the audit to revise and strengthen your organization’s security policies. This may involve updating access controls, refining password policies, revising data retention practices, or enhancing incident response procedures. Applying tips for network security audit at this stage ensures your security framework stays aligned with emerging threats and evolving compliance standards, keeping your organization protected and audit-ready.
Conduct Training
One of the most impactful tips for network security audit implementation is investing in employee training. Share the findings with your team and offer tailored workshops or sessions that address the specific gaps identified during the audit. Employees serve as the frontline in protecting your network, making it essential that they are well-informed and consistently adhere to cybersecurity best practices.
Schedule Re-audits
Security isn’t a one-time event. Schedule follow-up audits at regular intervals—quarterly, semi-annually, or annually depending on your risk profile. Re-audits help measure progress, detect new vulnerabilities, and reinforce a culture of continuous improvement.
Long-Term Gains from Short-Term Actions
When you consistently apply these tips for network security audit, you’re doing more than just preventing cyberattacks. You’re building a resilient and adaptive cybersecurity posture that safeguards your organization’s long-term success in an increasingly digital world.
Tools and Software That Simplify Network Security Audits
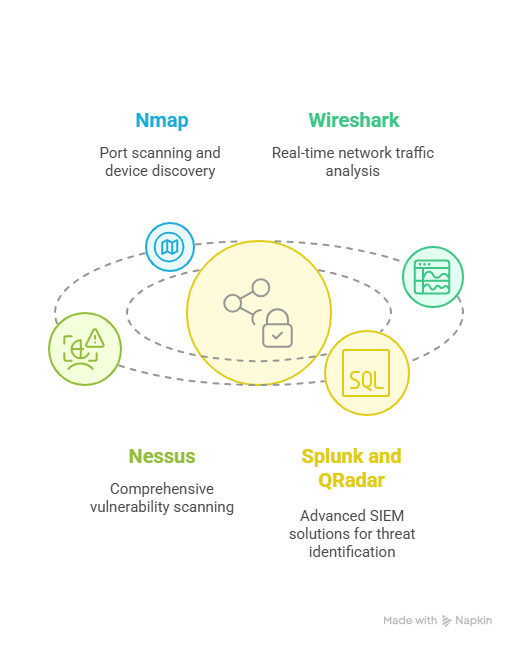
Leveraging the right technology significantly boosts both the accuracy and productivity of your audit process. Popular tools include:
- Nmap: For port scanning and device discovery.
- Wireshark: To analyze network traffic in real time.
- Nessus: Comprehensive vulnerability scanning.
- Splunk and QRadar: Advanced SIEM solutions used to correlate logs and identify potential security threats in real-time.
Choosing the right tools based on your network size and security goals is one of the smartest tips for network security audit execution.
How Elysian Communication Can Help
Here’s how we support your journey to stronger network defense:
- Comprehensive Network Security Audits
Our audits go beyond surface-level scans. We conduct deep assessments of your network, identifying vulnerabilities, misconfigurations, outdated protocols, and compliance gaps. - Customized Security Architecture Development
One-size-fits-all doesn’t work in cybersecurity. Our team designs tailored security infrastructures that integrate seamlessly with your existing operations while scaling with your growth. - Regulatory Compliance Support (ISO, HIPAA, GDPR, and more)
Stay audit-ready and compliant with evolving standards. We help you navigate complex regulatory landscapes with full documentation, gap analysis, and policy alignment.
Unlike standard service providers, Elysian Communication offers tailored, data-backed solutions that directly support your strategic business goals. With extensive industry experience, our team applies proven tips for network security audit in every project, ensuring comprehensive protection and measurable results for your IT infrastructure.
Conclusion: Secure Your Digital Future with Effective Auditing
Cybersecurity isn’t a one-time activity—it’s a continuous journey. Whether you’re a startup or a multinational enterprise, implementing these tips for network security audit will ensure your digital assets are protected against evolving threats.
From preparation and execution to remediation and re-evaluation, each step plays a vital role in your security posture. Partner with Elysian Communication to access expert audits, cutting-edge tools, and a proactive defense approach.
Don’t wait for a breach to test your defenses—start your network security audit today and take the first step toward a safer tomorrow.





